If you want to access email batan.go.id domain, please follow instructions below.
For Microsoft Outlook users :
Incoming Mail (POP3) : mail.batan.go.id
Outgoing mail (SMTP) : mail.batan.go.id
Server port number for SMTP: 25
This server requires a secure connection (SSL) : enable
Server port number for POP3: 995
This server requires a secure connection (SSL) : enable
For Thunderbirds user :
Incoming : mail.batan.go.id, POP, 110, STARTTLS
Outgoing : mail.batan.go.id, SMTP, 25, STARTTLS
For Mail in Mac OS :
Click menu Mail then Preferences
Type = POP or IMAP
incoming mail server = mail.batan.go.id
SMTP
Outgoing mail server = mail.batan.go.id
19 May 2011
Comparison Movie Recording between DSLR and Handycam
In this article, I'll compare the movie-making between DSLR Camera and Handycam. I used DSLR Camera Canon EOS 550D and handycam Sony DCR SR-45.
Video recording with DSLR Camera Canon EOS 550D
Movie rec. size = 1920 x 1080
36,2 MB = 6 sec -> 6,03 MB per sec
45,9 MB = 8 sec -> 5,74 MB per sec
36,0 MB = 6 sec -> 6,00 MB per sec
Error message : Movie recording has been stopped automatically
Movie rec. size = 1280 x 720
33.5 MB = 6 sec -> 5,58 MB per sec
35.2 MB = 6 sec -> 5.87 MB per sec
30.1 MB = 5 sec -> 6,02 MB per sec
Error message : Movie recording has been stopped automatically
Movie rec. size = 640 x 480
59.8 MB = 22 sec -> 2.71 MB per sec
80.5 MB = 31 sec -> 2,60 MB per sec
27,9 MB = 10 sec -> 2,79 MB per sec
No error message.
Canon EOS 550D has file format MVI_xxxx.MOV dan MVI_xxxx.THM
Video recording with Handycam Sony DCR SR-45
Movie rec. size ?
15,0 MB = 19 sec -> 0,79 MB per sec
19,5 MB = 23 sec -> 0,85 MB per sec
69,0 MB = 82 sec -> 0,84 MB per sec
File format : M2Uxxxxx.MPG
Video recording with DSLR Camera Canon EOS 550D
Movie rec. size = 1920 x 1080
36,2 MB = 6 sec -> 6,03 MB per sec
45,9 MB = 8 sec -> 5,74 MB per sec
36,0 MB = 6 sec -> 6,00 MB per sec
Error message : Movie recording has been stopped automatically
Movie rec. size = 1280 x 720
33.5 MB = 6 sec -> 5,58 MB per sec
35.2 MB = 6 sec -> 5.87 MB per sec
30.1 MB = 5 sec -> 6,02 MB per sec
Error message : Movie recording has been stopped automatically
Movie rec. size = 640 x 480
59.8 MB = 22 sec -> 2.71 MB per sec
80.5 MB = 31 sec -> 2,60 MB per sec
27,9 MB = 10 sec -> 2,79 MB per sec
No error message.
Canon EOS 550D has file format MVI_xxxx.MOV dan MVI_xxxx.THM
Video recording with Handycam Sony DCR SR-45
Movie rec. size ?
15,0 MB = 19 sec -> 0,79 MB per sec
19,5 MB = 23 sec -> 0,85 MB per sec
69,0 MB = 82 sec -> 0,84 MB per sec
File format : M2Uxxxxx.MPG
18 May 2011
How To Install Adobe Acrobat Reader in Fedora 13 and Previous Versions
This brief tutorial will show you how to easily install Adobe Acrobat PDF Reader in Fedora 13, codenamed Goddard. There are many ways to install Adobe Reader in Fedora, but this method is the easiest. After installing you will be able to open PDF documents with Adobe PDF Reader.
See more : http://www.liberiangeek.net/2010/06/how-to-install-adobe-acrobat-reader-in-fedora-13-and-previous-versions/
See more : http://www.liberiangeek.net/2010/06/how-to-install-adobe-acrobat-reader-in-fedora-13-and-previous-versions/
15 May 2011
Computer Security Devices
To protect your network computer, you can use devices such as IPS HP Tipping Point S110, BlueCoat Proxy SG/ProxyAV, Citrix NetScaler, Tufin T-500, Riverbed SteelHead. The function and position on LAN of every device, is different.
The AppDV security solution is just one part of our HP TippingPoint comprehensive application security portfolio comprised of our Intrusion Prevention System (IPS), Security Management System (SMS), and hundreds of Digital Vaccines developed by DVLabs - all designed to help you manage and protect your vulnerable applications and your network from exploits and attacks.
The Blue Coat ProxySG appliance represents the latest in perimeter defense for securing and controlling Web-based content and applications. The Blue Coat ProxySG was designed to integrate protection and control functions for Internet and intranet traffic without sacrificing performance and employee productivity.
Citrix© NetScaler© is an all-in-one Web application delivery solution that makes applications run five times better by ensuring application availability through advanced L4-7 traffic management, by increasing security with an integrated application firewall and by substantially lowering costs by offloading servers. This reduces TCO, optimizes the user experience and makes sure that applications are always available. See more.
Tufin's SecureTrack provides configuration change monitoring, reporting, and alerting features specifically for corporate firewalls. Check Point (NG FP3+), Cisco (PIX, ASA, FWSM, IOS Routers), Juniper (ScreenOS), and soon Fortinet (FortiGate) firewalls are all supported. (How about MikroTik RouterBoard?)
The product is deployed on a central Red Hat (Enterprise Linux, CentOS) server. For Check Point firewalls, the product tracks all changes made by admins (watching for policy saves or installs) logged onto a Check Point SmartDashboard or Provider-1 GUI. When such changes are noted, the central server uses OPSEC to retrieve the policy, storing it in its own internal DB for subsequent analysis. For other supported firewalls, the product periodically logs into the firewall via SSH, retrieving the firewall's policies and ACLs and translating them into the product's internal XML rule base format. See more.
Riverbed Technology positions itself as being in the business of providing performance improvements to networked environments. Riverbed's WAN optimization products, both appliance-based and virtual, are branded under the product name Steelhead. The company differentiates itself in the market in part based on the relationships that it has with key technology partners, including Microsoft, EMC, HP, IBM and VMware. See more.
Price List
The AppDV security solution is just one part of our HP TippingPoint comprehensive application security portfolio comprised of our Intrusion Prevention System (IPS), Security Management System (SMS), and hundreds of Digital Vaccines developed by DVLabs - all designed to help you manage and protect your vulnerable applications and your network from exploits and attacks.
The Blue Coat ProxySG appliance represents the latest in perimeter defense for securing and controlling Web-based content and applications. The Blue Coat ProxySG was designed to integrate protection and control functions for Internet and intranet traffic without sacrificing performance and employee productivity.
Citrix© NetScaler© is an all-in-one Web application delivery solution that makes applications run five times better by ensuring application availability through advanced L4-7 traffic management, by increasing security with an integrated application firewall and by substantially lowering costs by offloading servers. This reduces TCO, optimizes the user experience and makes sure that applications are always available. See more.
Tufin's SecureTrack provides configuration change monitoring, reporting, and alerting features specifically for corporate firewalls. Check Point (NG FP3+), Cisco (PIX, ASA, FWSM, IOS Routers), Juniper (ScreenOS), and soon Fortinet (FortiGate) firewalls are all supported. (How about MikroTik RouterBoard?)
The product is deployed on a central Red Hat (Enterprise Linux, CentOS) server. For Check Point firewalls, the product tracks all changes made by admins (watching for policy saves or installs) logged onto a Check Point SmartDashboard or Provider-1 GUI. When such changes are noted, the central server uses OPSEC to retrieve the policy, storing it in its own internal DB for subsequent analysis. For other supported firewalls, the product periodically logs into the firewall via SSH, retrieving the firewall's policies and ACLs and translating them into the product's internal XML rule base format. See more.
Riverbed Technology positions itself as being in the business of providing performance improvements to networked environments. Riverbed's WAN optimization products, both appliance-based and virtual, are branded under the product name Steelhead. The company differentiates itself in the market in part based on the relationships that it has with key technology partners, including Microsoft, EMC, HP, IBM and VMware. See more.
Price List
- HP Tipping Point S110, US$9,289.99
- Blue Coat ProxySG 300 Series SG300-25 - security appliance, USD $8,780.99
- Citrix Netscaler NS 7000 Security Access Gateway, US $3,999.99
- Tufin T-500 Appliance (Up to 100 firewalls, Quad-Core Intel® Xeon®, 8GB RAM, 1U, Dual PSU, RAID, 1-Year Support and Advanced Replacement Program Warranty), US$5,300
- Riverbed Steelhead 1050-L (SHA-01050-L) with 4 onboard GbE bypass ports (800 conn/6Mbps), US$12,972. Can use single Steelhead? Or need a pair?
14 May 2011
Anything about MikroTik Hotspot
Articles related with Mikrotik hotspot such as :
HotSpot Gateway Documentation
Manual:IP/Hotspot
http://www.settingmikrotik.com/
Step by Step Setup Hotspot dengan Halaman Login di Mikrotik Router OS
Konfigurasi Hotspot Mikrotik
How to Setup Your Own Hotspot with MIKROTIK routers
Mikrotik Hotspot dan User Manager
Cara hack hotspot mikrotik
Mikrotik Hotspot Hacking
Setting Radius dan hotspot Mikrotik
HotSpot Gateway Documentation
Manual:IP/Hotspot
http://www.settingmikrotik.com/
Step by Step Setup Hotspot dengan Halaman Login di Mikrotik Router OS
Konfigurasi Hotspot Mikrotik
How to Setup Your Own Hotspot with MIKROTIK routers
Mikrotik Hotspot dan User Manager
Cara hack hotspot mikrotik
Mikrotik Hotspot Hacking
Setting Radius dan hotspot Mikrotik
10 May 2011
The Meaning of MikroTik Log Messages on Linux Server
This is example of log messages from MikroTik. I am trying to understand the causes of these logs and the rule where the Mikrotik that produce it. I tried to group them in the same time sequence.
May 9 23:43:46 183.91.67.2 KPB Unknown(81) = 00-00-00-42-50-41-2D-41-47-2D-50-43
May 9 23:43:46 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 9 23:43:46 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific
May 9 23:43:46 KPB dhcp_bsdm sending ack with id 1548336385 to 255.255.255.255
May 9 23:43:46 183.91.67.2 KPB flags = broadcast
May 9 23:43:46 183.91.67.2 KPB ciaddr = 0.0.0.0
May 9 23:43:46 183.91.67.2 KPB yiaddr = 192.168.2.85
May 9 23:43:46 183.91.67.2 KPB siaddr = 192.168.2.1
May 9 23:43:46 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 9 23:43:46 183.91.67.2 KPB Msg-Type = ack
May 9 23:43:46 183.91.67.2 KPB Server-Id = 192.168.2.1
May 9 23:43:46 183.91.67.2 KPB Address-Time = 31536000
May 9 23:43:46 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 9 23:43:46 183.91.67.2 KPB Router = 192.168.2.1
May 9 23:43:46 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 9 23:58:08 KPB dhcp_bu received inform with id 420795606 from 192.168.1.246
May 9 23:58:08 183.91.67.2 KPB Msg-Type = inform
May 9 23:58:08 183.91.67.2 KPB Client-Id = 01-00-50-8D-9F-48-F9
May 9 23:58:08 183.91.67.2 KPB Host-Name = "Windows7-PC"
May 9 23:58:08 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 9 23:58:08 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific,Unknown(252)
May 9 23:58:08 KPB dhcp_bu sending ack with id 420795606 to 255.255.255.255
May 9 23:58:08 183.91.67.2 KPB flags = broadcast
May 9 23:58:08 183.91.67.2 KPB ciaddr = 192.168.1.246
May 9 23:58:08 183.91.67.2 KPB siaddr = 192.168.1.129
May 9 23:58:08 183.91.67.2 KPB chaddr = 00:50:8D:9F:48:F9
May 9 23:58:08 183.91.67.2 KPB Msg-Type = ack
May 9 23:58:08 183.91.67.2 KPB Server-Id = 192.168.1.129
May 9 23:58:08 183.91.67.2 KPB Subnet-Mask = 255.255.255.128
May 9 23:58:08 183.91.67.2 KPB Router = 192.168.1.129
May 9 23:58:08 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:14:15 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:14:15 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:14:15 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:18:50 KPB dhcp_bsdm received request with id 2652037990 from 0.0.0.0
May 10 00:18:50 183.91.67.2 KPB flags = broadcast
May 10 00:18:50 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:18:50 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:18:50 183.91.67.2 KPB Msg-Type = request
May 10 00:18:50 183.91.67.2 KPB Client-Id = 01-00-15-F2-82-D9-39
May 10 00:18:50 183.91.67.2 KPB Address-Request = 192.168.2.85
May 10 00:18:50 183.91.67.2 KPB Host-Name = "BPA-AG-PC"
May 10 00:18:50 183.91.67.2 KPB Unknown(81) = 00-00-00-42-50-41-2D-41-47-2D-50-43
May 10 00:18:50 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 10 00:18:50 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific
May 10 00:18:50 KPB dhcp_bsdm sending ack with id 2652037990 to 255.255.255.255
May 10 00:18:50 183.91.67.2 KPB flags = broadcast
May 10 00:18:50 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:18:50 183.91.67.2 KPB yiaddr = 192.168.2.85
May 10 00:18:50 183.91.67.2 KPB siaddr = 192.168.2.1
May 10 00:18:50 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:18:50 183.91.67.2 KPB Msg-Type = ack
May 10 00:18:50 183.91.67.2 KPB Server-Id = 192.168.2.1
May 10 00:18:50 183.91.67.2 KPB Address-Time = 31536000
May 10 00:18:50 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:18:50 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:18:50 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:31:37 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:31:37 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:31:37 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:31:48 KPB dhcp_bsdm received request with id 3594588014 from 0.0.0.0
May 10 00:31:48 183.91.67.2 KPB flags = broadcast
May 10 00:31:48 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:31:48 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:31:48 183.91.67.2 KPB Msg-Type = request
May 10 00:31:48 183.91.67.2 KPB Client-Id = 01-00-15-F2-82-D9-39
May 10 00:31:48 183.91.67.2 KPB Address-Request = 192.168.2.85
May 10 00:31:48 183.91.67.2 KPB Host-Name = "BPA-AG-PC"
May 10 00:31:48 183.91.67.2 KPB Unknown(81) = 00-00-00-42-50-41-2D-41-47-2D-50-43
May 10 00:31:48 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 10 00:31:48 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific
May 10 00:31:48 KPB dhcp_bsdm sending ack with id 3594588014 to 255.255.255.255
May 10 00:31:48 183.91.67.2 KPB flags = broadcast
May 10 00:31:48 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:31:48 183.91.67.2 KPB yiaddr = 192.168.2.85
May 10 00:31:48 183.91.67.2 KPB siaddr = 192.168.2.1
May 10 00:31:48 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:31:48 183.91.67.2 KPB Msg-Type = ack
May 10 00:31:48 183.91.67.2 KPB Server-Id = 192.168.2.1
May 10 00:31:48 183.91.67.2 KPB Address-Time = 31536000
May 10 00:31:48 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:31:48 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:31:48 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 01:24:12 183.91.67.2 KPB Server-Id = 192.168.1.129
May 10 01:24:12 183.91.67.2 KPB Subnet-Mask = 255.255.255.128
May 10 01:24:12 183.91.67.2 KPB Router = 192.168.1.129
May 10 01:24:12 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 02:11:24 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 02:11:24 183.91.67.2 KPB Router = 192.168.2.1
May 10 02:11:24 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 02:50:02 SRP HotSpot_Gd71: new host detected 00:14:D1:F1:16:8B/192.168.1.19 by UDP :1026 -> 202.169.224.16:123
May 10 02:55:02 SRP HotSpot_Gd71: dynamic host 172.16.1.114 removed: idle timeout
May 10 03:00:31 183.91.67.2 KPB Subnet-Mask = 255.255.255.128
May 10 03:00:31 183.91.67.2 KPB Router = 192.168.1.129
May 10 03:00:31 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 03:21:38 183.91.67.2 KPB Address-Time = 31536000
May 10 03:21:38 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 03:21:38 183.91.67.2 KPB Router = 192.168.2.1
May 10 03:21:38 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 03:49:08 KPB user admin logged in from 110.137.227.147 via winbox
May 10 03:51:12 KPB log rule changed by admin
May 10 03:51:18 KPB log rule changed by admin
May 10 03:51:23 KPB log rule changed by admin
From http://whois.domaintools.com/, I find :
202.152.5.36 = ns.idola.net.id
202.152.0.2 = rajawali.idola.net.id
For last 100 lines :
#tail -100 /var/log/mikrotik.log
For real time :
#tail -f /var/log/mikrotik.log
Tested : event, info, system and warning
I tried to disable log rule or under testing : critical, dhcp, error
Enable log rule : hotspot.
May 9 23:43:46 183.91.67.2 KPB Unknown(81) = 00-00-00-42-50-41-2D-41-47-2D-50-43
May 9 23:43:46 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 9 23:43:46 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific
May 9 23:43:46 KPB dhcp_bsdm sending ack with id 1548336385 to 255.255.255.255
May 9 23:43:46 183.91.67.2 KPB flags = broadcast
May 9 23:43:46 183.91.67.2 KPB ciaddr = 0.0.0.0
May 9 23:43:46 183.91.67.2 KPB yiaddr = 192.168.2.85
May 9 23:43:46 183.91.67.2 KPB siaddr = 192.168.2.1
May 9 23:43:46 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 9 23:43:46 183.91.67.2 KPB Msg-Type = ack
May 9 23:43:46 183.91.67.2 KPB Server-Id = 192.168.2.1
May 9 23:43:46 183.91.67.2 KPB Address-Time = 31536000
May 9 23:43:46 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 9 23:43:46 183.91.67.2 KPB Router = 192.168.2.1
May 9 23:43:46 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 9 23:58:08 KPB dhcp_bu received inform with id 420795606 from 192.168.1.246
May 9 23:58:08 183.91.67.2 KPB Msg-Type = inform
May 9 23:58:08 183.91.67.2 KPB Client-Id = 01-00-50-8D-9F-48-F9
May 9 23:58:08 183.91.67.2 KPB Host-Name = "Windows7-PC"
May 9 23:58:08 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 9 23:58:08 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific,Unknown(252)
May 9 23:58:08 KPB dhcp_bu sending ack with id 420795606 to 255.255.255.255
May 9 23:58:08 183.91.67.2 KPB flags = broadcast
May 9 23:58:08 183.91.67.2 KPB ciaddr = 192.168.1.246
May 9 23:58:08 183.91.67.2 KPB siaddr = 192.168.1.129
May 9 23:58:08 183.91.67.2 KPB chaddr = 00:50:8D:9F:48:F9
May 9 23:58:08 183.91.67.2 KPB Msg-Type = ack
May 9 23:58:08 183.91.67.2 KPB Server-Id = 192.168.1.129
May 9 23:58:08 183.91.67.2 KPB Subnet-Mask = 255.255.255.128
May 9 23:58:08 183.91.67.2 KPB Router = 192.168.1.129
May 9 23:58:08 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:14:15 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:14:15 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:14:15 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:18:50 KPB dhcp_bsdm received request with id 2652037990 from 0.0.0.0
May 10 00:18:50 183.91.67.2 KPB flags = broadcast
May 10 00:18:50 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:18:50 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:18:50 183.91.67.2 KPB Msg-Type = request
May 10 00:18:50 183.91.67.2 KPB Client-Id = 01-00-15-F2-82-D9-39
May 10 00:18:50 183.91.67.2 KPB Address-Request = 192.168.2.85
May 10 00:18:50 183.91.67.2 KPB Host-Name = "BPA-AG-PC"
May 10 00:18:50 183.91.67.2 KPB Unknown(81) = 00-00-00-42-50-41-2D-41-47-2D-50-43
May 10 00:18:50 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 10 00:18:50 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific
May 10 00:18:50 KPB dhcp_bsdm sending ack with id 2652037990 to 255.255.255.255
May 10 00:18:50 183.91.67.2 KPB flags = broadcast
May 10 00:18:50 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:18:50 183.91.67.2 KPB yiaddr = 192.168.2.85
May 10 00:18:50 183.91.67.2 KPB siaddr = 192.168.2.1
May 10 00:18:50 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:18:50 183.91.67.2 KPB Msg-Type = ack
May 10 00:18:50 183.91.67.2 KPB Server-Id = 192.168.2.1
May 10 00:18:50 183.91.67.2 KPB Address-Time = 31536000
May 10 00:18:50 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:18:50 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:18:50 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:31:37 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:31:37 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:31:37 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:31:48 KPB dhcp_bsdm received request with id 3594588014 from 0.0.0.0
May 10 00:31:48 183.91.67.2 KPB flags = broadcast
May 10 00:31:48 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:31:48 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:31:48 183.91.67.2 KPB Msg-Type = request
May 10 00:31:48 183.91.67.2 KPB Client-Id = 01-00-15-F2-82-D9-39
May 10 00:31:48 183.91.67.2 KPB Address-Request = 192.168.2.85
May 10 00:31:48 183.91.67.2 KPB Host-Name = "BPA-AG-PC"
May 10 00:31:48 183.91.67.2 KPB Unknown(81) = 00-00-00-42-50-41-2D-41-47-2D-50-43
May 10 00:31:48 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 10 00:31:48 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific
May 10 00:31:48 KPB dhcp_bsdm sending ack with id 3594588014 to 255.255.255.255
May 10 00:31:48 183.91.67.2 KPB flags = broadcast
May 10 00:31:48 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:31:48 183.91.67.2 KPB yiaddr = 192.168.2.85
May 10 00:31:48 183.91.67.2 KPB siaddr = 192.168.2.1
May 10 00:31:48 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:31:48 183.91.67.2 KPB Msg-Type = ack
May 10 00:31:48 183.91.67.2 KPB Server-Id = 192.168.2.1
May 10 00:31:48 183.91.67.2 KPB Address-Time = 31536000
May 10 00:31:48 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:31:48 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:31:48 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 01:24:12 183.91.67.2 KPB Server-Id = 192.168.1.129
May 10 01:24:12 183.91.67.2 KPB Subnet-Mask = 255.255.255.128
May 10 01:24:12 183.91.67.2 KPB Router = 192.168.1.129
May 10 01:24:12 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 02:11:24 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 02:11:24 183.91.67.2 KPB Router = 192.168.2.1
May 10 02:11:24 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 02:50:02 SRP HotSpot_Gd71: new host detected 00:14:D1:F1:16:8B/192.168.1.19 by UDP :1026 -> 202.169.224.16:123
May 10 02:55:02 SRP HotSpot_Gd71: dynamic host 172.16.1.114 removed: idle timeout
May 10 03:00:31 183.91.67.2 KPB Subnet-Mask = 255.255.255.128
May 10 03:00:31 183.91.67.2 KPB Router = 192.168.1.129
May 10 03:00:31 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 03:21:38 183.91.67.2 KPB Address-Time = 31536000
May 10 03:21:38 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 03:21:38 183.91.67.2 KPB Router = 192.168.2.1
May 10 03:21:38 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 03:49:08 KPB user admin logged in from 110.137.227.147 via winbox
May 10 03:51:12 KPB log rule changed by admin
May 10 03:51:18 KPB log rule changed by admin
May 10 03:51:23 KPB log rule changed by admin
From http://whois.domaintools.com/, I find :
202.152.5.36 = ns.idola.net.id
202.152.0.2 = rajawali.idola.net.id
For last 100 lines :
#tail -100 /var/log/mikrotik.log
For real time :
#tail -f /var/log/mikrotik.log
Tested : event, info, system and warning
I tried to disable log rule or under testing : critical, dhcp, error
Enable log rule : hotspot.
07 May 2011
Send Logs MikroTik with Private IP to Linux Server
 Basically, MikroTik with Private IP can send log to Linux Server. With condition, this MikroTik with Private IP, has uplink to another MikroTik with Public IP. Suppose MikroTik RB1100 with Private IP was called SRP and has IP 192.168.1.2. Suppose MikroTik RB1100 with Public IP was called NOC and has IP 183.91.x1.y1. Because IP 183.91.x1.y1 already be set in the file /etc/rsyslog.conf, then on the linux server side does not need to apply the settings again. You just need setting up on the MikroTik SRP.
Basically, MikroTik with Private IP can send log to Linux Server. With condition, this MikroTik with Private IP, has uplink to another MikroTik with Public IP. Suppose MikroTik RB1100 with Private IP was called SRP and has IP 192.168.1.2. Suppose MikroTik RB1100 with Public IP was called NOC and has IP 183.91.x1.y1. Because IP 183.91.x1.y1 already be set in the file /etc/rsyslog.conf, then on the linux server side does not need to apply the settings again. You just need setting up on the MikroTik SRP.On Linux Server, lets /etc/rsyslog.conf file like this
### for mikrotik remote logging
$AllowedSender UDP, 183.91.x1.y1/255.255.255.255
$AllowedSender TCP, 183.91.x1.y1/255.255.255.255
$UDPSenverAddress 183.91.x1.y1
$UDPSenverRun 514
:fromhost-ip, isequal, "183.91.x1.y1" /var/log/mikrotik.log
& ~
On MikroTik SRP
1. Set action from /system logging menu
Name: lognhc
Type: remote
Remote Address: 183.91.x2.y2 (nhc server)
Remote Port: 514
BSD Syslog: enable
Syslog Facility: 3 (daemon)
2. Set Log Rules from /system logging menu
Topics: system
Prefix:
Action: lognhc
Other topics : critical, dhcp, error, event, hotspot, info, system, warning
Already configured: KPB, SRP.
Check the result:

Send Logs MikroTik to Linux Server
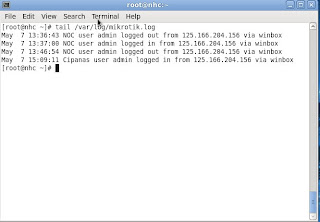 To send remote logging from a MikroTik device to a Linux Server, you must configure on both sides. Its setting itself is very simple but quite confusing for some people. Lets read carefully. I use MikroTik RB1000, RB1100 and RB450G. All kind of these MikroTik like same way to setting.
To send remote logging from a MikroTik device to a Linux Server, you must configure on both sides. Its setting itself is very simple but quite confusing for some people. Lets read carefully. I use MikroTik RB1000, RB1100 and RB450G. All kind of these MikroTik like same way to setting.On Linux Server
[root@nhc ~]# uname -a
Linux nhc.batan.go.id 2.6.25-14.fc9.i686 #1 SMP Thu May 1 06:28:41 EDT 2008 i686 i686 i386 GNU/Linux
[root@nhc ~]# yum install rsyslog
[root@nhc ~]# /etc/rc.d/init.d/rsyslog restart
[root@nhc ~]# mcedit /etc/rsyslog.conf
------------------------------------------------
# Provides UDP syslog reception
# unremark 2 lines below by MSM, 7 May 2011
$ModLoad imudp.so
$UDPServerRun 514
### for mikrotik remote logging
$AllowedSender UDP, 183.91.67.2/255.255.255.255
$AllowedSender TCP, 183.91.67.2/255.255.255.255
$UDPSenverAddress 183.91.67.2
$UDPSenverRun 514
:fromhost-ip, isequal, "183.91.67.2" /var/log/mikrotik.log
& ~
------------------------------------------------
Restart rsyslog daemon :
[root@nhc ~]# /etc/rc.d/init.d/rsyslog restart
On MikroTik
1. Set action from /system logging menu
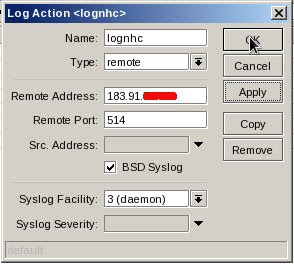 Name: lognhc
Name: lognhcType: remote
Remote Address: 183.91.70.165 (nhc server)
Remote Port: 514
BSD Syslog: enable
Syslog Facility: 3 (daemon)
2. Set Log Rules from /system logging menu
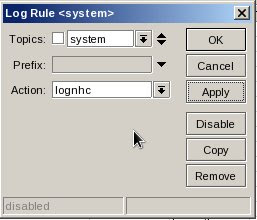 Topics: system
Topics: systemPrefix:
Action: lognhc
Other topics : critical, dhcp, error, event, hotspot, info, system, warning
Checking the results:
[root@nhc ~]# tail /var/log/mikrotik.log
May 7 13:36:43 NOC user admin logged out from 125.166.204.156 via winbox
May 7 13:37:00 NOC user admin logged in from 125.166.204.156 via winbox
May 7 13:46:54 NOC user admin logged out from 125.166.204.156 via winbox
To add another mikrotik device
To add more mikrotik devices, just add this command or syntax below to /etc/rsyslog.conf file.
### for cipanas mikrotik remote logging
$AllowedSender UDP, 110.136.158.148/255.255.255.255
$AllowedSender TCP, 110.136.158.148/255.255.255.255
$UDPSenverAddress 110.136.158.148
$UDPSenverRun 514
:fromhost-ip, isequal, "110.136.158.148" /var/log/mikrotik.log
& ~
Don't forget to
1. Restart daemon on Linux Server
[root@nhc ~]# /etc/rc.d/init.d/rsyslog restart
2. Add Action on Mikrotik /system logging (see sample above)
3. Add Log Rules on Mikrotik /system logging (see sample above)
4. Checking the results
[root@nhc ~]# tail /var/log/mikrotik.log
May 7 13:36:43 NOC user admin logged out from 125.166.204.156 via winbox
May 7 13:37:00 NOC user admin logged in from 125.166.204.156 via winbox
May 7 13:46:54 NOC user admin logged out from 125.166.204.156 via winbox
May 7 15:09:11 Cipanas user admin logged in from 125.166.204.156 via winbox
See :
http://handz106.multiply.com/journal/item/83/Mikrotik_remote_logging_and_rsyslog
Next Problem :
How to send logs from MikroTik with Private IP
Send Log From MikroTik with Private IP
MikroTik with Private IP has uplink to MikroTik with Public IP. Suppose MikroTik with Private IP is SRP. And suppose MikroTik with Public IP is NOC. SRP has IP 192.168.1.2. NOC has IP 183.91.67.2. Because IP 183.91.67.2 already be set in the file /etc/rsyslog.conf, then on the linux server side does not need to apply the settings again. You just need setting up on the MikroTik SRP.
On Linux Server, /etc/rsyslog.conf file
### for mikrotik remote logging
$AllowedSender UDP, 183.91.67.2/255.255.255.255
$AllowedSender TCP, 183.91.67.2/255.255.255.255
$UDPSenverAddress 183.91.67.2
$UDPSenverRun 514
:fromhost-ip, isequal, "183.91.67.2" /var/log/mikrotik.log
& ~
On MikroTik SRP
1. Set action from /system logging menu
Name: lognhc
Type: remote
Remote Address: 183.91.70.165 (nhc server)
Remote Port: 514
BSD Syslog: enable
Syslog Facility: 3 (daemon)
2. Set Log Rules from /system logging menu
Topics: system
Prefix:
Action: lognhc
Other topics : critical, dhcp, error, event, hotspot, info, system, warning
How to Change language settings in Windows XP
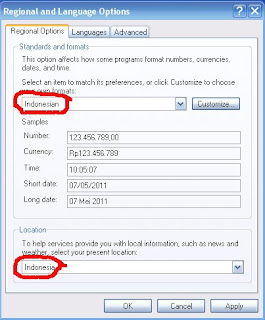 This article describes how to change the language in Windows XP. Setting the language does not change the language of Windows menus and dialogs, but it does allow you to display text in other languages and to enter text in other languages. Some languages (typically Asian languages) will not appear correctly in the eWebEditPro menus and dialogs unless the default language matches the language of the eWebEditPro locale XML data. Multiple languages will appear in the editor's content Window regardless of the language chosen for the menus and dialogs.
This article describes how to change the language in Windows XP. Setting the language does not change the language of Windows menus and dialogs, but it does allow you to display text in other languages and to enter text in other languages. Some languages (typically Asian languages) will not appear correctly in the eWebEditPro menus and dialogs unless the default language matches the language of the eWebEditPro locale XML data. Multiple languages will appear in the editor's content Window regardless of the language chosen for the menus and dialogs.Changing the language does not change the language of the menus and dialogs of Windows or Windows applications like Internet Explorer. For more information on changing the language of Windows itself and IE, see the references below.
Language settings in Windows 95/98/Me are significantly different and beyond the scope of this article. Windows NT does not support fully changing the language from English to Asian. The native version of Windows NT is required to use Japanese, Chinese, or Korean.
Set a default language of the system to match the language you wish to display. You may need to install the language from the Windows Setup CD-ROM. You may need to restart Windows after selecting a new system language.
Steps to change the default system language (Windows XP)
- Open the Control Panel.
- Open Regional and Language Options.
- Click the Languages tab.
- Ensure Supplemental language support items are checked.
- Click the Advanced tab.
- Select the language from the list in the Language for non-Unicode programs.
Send Logs MikroTik to Email
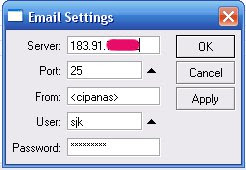 MikroTik logs are not stored permanently in the memory MikroTik, because storage space reasons. While there are some very important logs for our. For this reason, we need to send logs to another system, such as email. To send logs to an email, you can use /tool email menu and /system logging menu.
MikroTik logs are not stored permanently in the memory MikroTik, because storage space reasons. While there are some very important logs for our. For this reason, we need to send logs to another system, such as email. To send logs to an email, you can use /tool email menu and /system logging menu.1. Set email account from /tool email menu
Server: 183.91.x.y (mail server address)
Port: 25
From: <cipanas>
User: sjk
Password:******
In this case, I want send email to sjk@mydomain.com, and I want the email sender is cipanas, where the router was placed.
2. Set action from /system logging menu
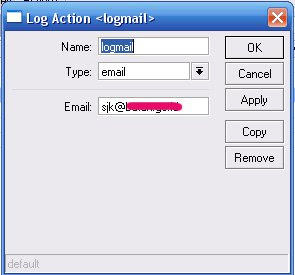
Name: logmail
Type: email
Email: sjk@mydomain.com
You can change "logmail" with your own word. And please change sjk@mydomain.com with your email address.
3. Set Log Rules from /system logging menu
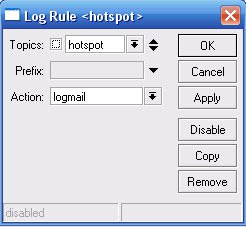
Topics: system
Prefix:
Action: logmail
Topics: hotspot
Prefix:
Action: logmail
Other topics : critical, dhcp, error, event, hotspot, info, system, warning, !debug.
Next effort : send logs to linux server, than show up on web server.
PSJ and BDG not set.
See :
http://handz106.multiply.com/journal/item/83/Mikrotik_remote_logging_and_rsyslog
06 May 2011
Problem with Maximum Resolution DELL U2711 Flat Panel Monitor
Setting the Maximum Resolution
If you have a Dell desktop or portable computer:
DELL U2711 have many input, that are :
I used VGA Card NVIDIA GeForce FX 5500 256MB with 2 input, VGA Input and DVI-D Input.
- Right-click on the desktop and select Properties.
- Select the Settings tab.
- Set the screen resolution to 2560 x 1440 (DVI and DisplayPort) or 2048 x 1152 (VGA) or 1080p (HDMI, Component).
- Click OK.
If you have a Dell desktop or portable computer:
- Go to support.dell.com, enter your service tag, and download the latest driver for your graphics card.
If you are using a non-Dell computer (portable or desktop):
- Go to the support site for your computer and download the latest graphic drivers.
- Go to your graphics card website and download the latest graphic drivers.
DELL U2711 have many input, that are :
- VGA input
- DVI-D 1 input
- DVI-D 2 input
- DisplayPort input
- HDMI input
- Component video input
- Composite video input

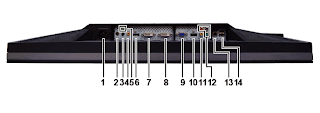
Bottom view
| Label | Description |
| 1 | AC power cord connector |
| 2 | DC power connector for Dell™ Soundbar |
| 3 | Audio out (rear) |
| 4 | Audio out (SUB/CTR) |
| 5 | Audio out (front) |
| 6 | DisplayPort connector |
| 7 | DVI connector-1 |
| 8 | DVI connector-2 |
| 9 | VGA connector |
| 10 | HDMI connector |
| 11 | Composite video connector |
| 12 | Component video connectors |
| 13 | USB upstream port |
| 14 | USB downstream ports |
I used VGA Card NVIDIA GeForce FX 5500 256MB with 2 input, VGA Input and DVI-D Input.
03 May 2011
Cain & Abel v4.9.35, Testing Results
 To test the security systems on multiple servers, I used Cain & Abel version 4.9.35 for Windows XP. Before I do the testing, I have to configure the program to select a specific adapter. For instance, I choose a NIC rather than a Wireless Adapter. Use the Configure menu -> click the Sniffer tab -> click \Device\NPF_bla bla bla -> OK. Choose the Sniffer tab, and than Start Sniffer icon. Check out HTTP group.
To test the security systems on multiple servers, I used Cain & Abel version 4.9.35 for Windows XP. Before I do the testing, I have to configure the program to select a specific adapter. For instance, I choose a NIC rather than a Wireless Adapter. Use the Configure menu -> click the Sniffer tab -> click \Device\NPF_bla bla bla -> OK. Choose the Sniffer tab, and than Start Sniffer icon. Check out HTTP group.The results :
Secure : Yahoo Mail, ssh to nhc, Pustaka Iptek, Blogger, Winbox
Unsecure : Webmail, ftp to nhc, SITP, SIPL,
No checked : wcm, raker, help desk sjk, hotspot
01 May 2011
Wireless LAN Security Summary
Wireless LAN Security Summary based on ISO 27001/ISO17799 are :
1. Develop an agency security policy that addresses the use of wireless technology, including 802.11.
A security policy is the foundation on which other countermeasures—the operational and technical ones—are rationalized and implemented. A documented security policy allows an organization to define acceptable architecture, implementation, and uses for 802.11 wireless technologies.
2. Ensure that users on the network are fully trained in computer security awareness and the risks associated with wireless technology (e.g., 802.11).
A security awareness program helps users to establish good security practices to prevent inadvertent or malicious intrusions into an organization’s information systems.
3. Perform a risk assessment to understand the value of the assets in the agency that need protection.
Understanding the value of organizational assets and the level of protection required is likely to enable more cost-effective wireless solutions that provide an appropriate level of security.
4. Ensure that the client NIC and AP support firmware upgrades so that security patches may be deployed as they become available (prior to purchase).
Wireless products should support upgrade and patching of firmware to be able to take advantage of wireless security enhancements and fixes.
5. Perform comprehensive security assessments at regular and random intervals (including validating that rogue APs do not exist in the 802.11 WLAN) to fully understand the wireless network security posture.
Security assessments, or audits, are an essential tool for checking the security posture of a WLAN and for determining corrective action to make sure it stays secure. Random checks ensure that the security posture is maintained beyond periods of assessment.
6. Ensure that external boundary protection is in place around the perimeter of the building or buildings of the agency.
The external boundaries should be secured to prevent malicious physical access to an organization’s information system infrastructure such as a fence or locked doors.
7. Deploy physical access controls to the building and other secure areas (e.g., using photo IDs or card badge readers).
Identification badges or physical access cards help to ensure that only authorized personnel have access to gain entry to a facility.
8. Complete a site survey to measure and establish the AP coverage for the agency.
Proper placement of Access Points will help ensure that there is adequate wireless coverage of the environment while minimizing exposure to external attack. The site survey should result in a report that proposes AP locations, determines coverage areas, and assigns radio channels to each AP and that ensures that the coverage range does not expose APs to potential malicious activities.
9. Take a complete inventory of all APs and 802.11 wireless devices.
A complete inventory list of APs and 802.11 wireless devices can be referenced when conducting an audit for unauthorized use of wireless technologies.
10. Ensure that wireless networks are not used until they comply with the agency’s security policy.
Security policy enforcement is vital for ensuring that only authorized APs and 802.11 wireless devices are operating in compliance with the organization’s wireless security policy.
Source : http://www.controlscada.com/download-free-iso-27001iso17799-wireless-lan-security-summary
1. Develop an agency security policy that addresses the use of wireless technology, including 802.11.
A security policy is the foundation on which other countermeasures—the operational and technical ones—are rationalized and implemented. A documented security policy allows an organization to define acceptable architecture, implementation, and uses for 802.11 wireless technologies.
2. Ensure that users on the network are fully trained in computer security awareness and the risks associated with wireless technology (e.g., 802.11).
A security awareness program helps users to establish good security practices to prevent inadvertent or malicious intrusions into an organization’s information systems.
3. Perform a risk assessment to understand the value of the assets in the agency that need protection.
Understanding the value of organizational assets and the level of protection required is likely to enable more cost-effective wireless solutions that provide an appropriate level of security.
4. Ensure that the client NIC and AP support firmware upgrades so that security patches may be deployed as they become available (prior to purchase).
Wireless products should support upgrade and patching of firmware to be able to take advantage of wireless security enhancements and fixes.
5. Perform comprehensive security assessments at regular and random intervals (including validating that rogue APs do not exist in the 802.11 WLAN) to fully understand the wireless network security posture.
Security assessments, or audits, are an essential tool for checking the security posture of a WLAN and for determining corrective action to make sure it stays secure. Random checks ensure that the security posture is maintained beyond periods of assessment.
6. Ensure that external boundary protection is in place around the perimeter of the building or buildings of the agency.
The external boundaries should be secured to prevent malicious physical access to an organization’s information system infrastructure such as a fence or locked doors.
7. Deploy physical access controls to the building and other secure areas (e.g., using photo IDs or card badge readers).
Identification badges or physical access cards help to ensure that only authorized personnel have access to gain entry to a facility.
8. Complete a site survey to measure and establish the AP coverage for the agency.
Proper placement of Access Points will help ensure that there is adequate wireless coverage of the environment while minimizing exposure to external attack. The site survey should result in a report that proposes AP locations, determines coverage areas, and assigns radio channels to each AP and that ensures that the coverage range does not expose APs to potential malicious activities.
9. Take a complete inventory of all APs and 802.11 wireless devices.
A complete inventory list of APs and 802.11 wireless devices can be referenced when conducting an audit for unauthorized use of wireless technologies.
10. Ensure that wireless networks are not used until they comply with the agency’s security policy.
Security policy enforcement is vital for ensuring that only authorized APs and 802.11 wireless devices are operating in compliance with the organization’s wireless security policy.
Source : http://www.controlscada.com/download-free-iso-27001iso17799-wireless-lan-security-summary
Comparison between COBIT, ITIL and ISO 27001
Many friend of mine keep asking me about what is should be implemented first to improve their information system management: whether taking Cobit, ITIL, or ISO27001. And the next question usually which one is the easiest to be implemented in their company.
To be able to answer this question, let me tell you the definition of this three major standard in information system, who has a little bit difference in basic concept.
COBIT
Cobit is stand for Control Objective over Information and Related Technology. Cobit issued by ISACA (Information System Control Standard) a non profit organization for IT Governance. The Cobit main function is to help the company, mapping their IT process to ISACA best practices standard. Cobit usually choosen by the company who performing information system audit, whether related to financial audit or general IT audit.
ITIL
ITIL is stand for Information Technology Library. ITIL issued by OGC, is a set of framework for managing IT Service Level. Although ITIL is quite similar with COBIT in many ways, but the basic difference is Cobit set the standard by seeing the process based and risk, and in the other hand ITIL set the standard from basic IT service.
ISO27001
ISO27001 is much more different between COBIT and ITIL, because ISO27001 is a security standard, so it has smaller but deeper domain compare to COBIT and ITIL.
Here is the detail table of comparison between this three standard
What should be implemented first?
There's no exact answer about this question, but i think its really depend on your company and your requirement. Most of company start to implemented Cobit first because its cover general information system. And after that they usually choose between ITIL or ISO27001.
Another consideration is about budget and authoritive. Cobit implementation usually run from internal audit budget and ITIL or ISO27001 usually performed using IT departement budget. This consideration usually makes what kind of standard to implemented first become depend on management policy.
What is the easiest standard?
From the implementatation view, ITIL is the easiest standard to be implemented. Because, ITIL could be implemented partially and still not have impact on performance. Example, if IT departement lack of budget and he could choose to implement IT Service Delivery layer only, and the next year he will try to implement IT Release Management or IT Problem Management.<
However COBIT and ISO27001 is quite difficult to be implemented partially, since it should see a process in bigger view first before they could implemented partially.
How to choose the right vendor?
Many vendor said that he could help your company to implement these standard effectively, in fact there is no one solution for all. Usually the COBIT vendor come from Publci Accounting Firm who has an IT Audit arm, eg PWC, DTT, KPMG, EY. This type of vendor is best choice for COBIT since they also work for COBIT implementation derivative such as COBIT for Sarbanes Oxley.
The other standard ITIL and ISO27001 usually come from General IT Consulting Company, eg. IBM, Accenture. And for ISO27001 most of IT networking company also could offer this standard consultation.
Do you have any other opinion with this comparison?
Others referrence:
ISACA: Aligning COBIT, ITIL and ISO 17799 for Business Benefit
Download Hundreds of Complimentary Industry Resources
Get hundreds of popular Industry magazines, white papers, webinars, podcasts, and more; all available at no cost to you. With more than 600 complimentary offers, you'll find plenty of titles to suit your professional interests and needs. Click Here and Sign up today!
Source : http://www.securityprocedure.com/
To be able to answer this question, let me tell you the definition of this three major standard in information system, who has a little bit difference in basic concept.
COBIT
Cobit is stand for Control Objective over Information and Related Technology. Cobit issued by ISACA (Information System Control Standard) a non profit organization for IT Governance. The Cobit main function is to help the company, mapping their IT process to ISACA best practices standard. Cobit usually choosen by the company who performing information system audit, whether related to financial audit or general IT audit.
ITIL
ITIL is stand for Information Technology Library. ITIL issued by OGC, is a set of framework for managing IT Service Level. Although ITIL is quite similar with COBIT in many ways, but the basic difference is Cobit set the standard by seeing the process based and risk, and in the other hand ITIL set the standard from basic IT service.
ISO27001
ISO27001 is much more different between COBIT and ITIL, because ISO27001 is a security standard, so it has smaller but deeper domain compare to COBIT and ITIL.
Here is the detail table of comparison between this three standard
| AREA | COBIT | ITIL | ISO27001 |
| Function | Mapping IT Process | Mapping IT Service Level Management | Information Security Framework |
| Area | 4 Process and 34 Domain | 9 Process | 10 Domain |
| Issuer | ISACA | OGC | ISO Board |
| Implementation | Information System Audit | Manage Service Level | Compliance to security standard |
| Consultant | Accounting Firm, IT Consulting Firm | IT Consulting firm | IT Consulting firm, Security Firm, Network Consultant |
What should be implemented first?
There's no exact answer about this question, but i think its really depend on your company and your requirement. Most of company start to implemented Cobit first because its cover general information system. And after that they usually choose between ITIL or ISO27001.
Another consideration is about budget and authoritive. Cobit implementation usually run from internal audit budget and ITIL or ISO27001 usually performed using IT departement budget. This consideration usually makes what kind of standard to implemented first become depend on management policy.
What is the easiest standard?
From the implementatation view, ITIL is the easiest standard to be implemented. Because, ITIL could be implemented partially and still not have impact on performance. Example, if IT departement lack of budget and he could choose to implement IT Service Delivery layer only, and the next year he will try to implement IT Release Management or IT Problem Management.<
However COBIT and ISO27001 is quite difficult to be implemented partially, since it should see a process in bigger view first before they could implemented partially.
How to choose the right vendor?
Many vendor said that he could help your company to implement these standard effectively, in fact there is no one solution for all. Usually the COBIT vendor come from Publci Accounting Firm who has an IT Audit arm, eg PWC, DTT, KPMG, EY. This type of vendor is best choice for COBIT since they also work for COBIT implementation derivative such as COBIT for Sarbanes Oxley.
The other standard ITIL and ISO27001 usually come from General IT Consulting Company, eg. IBM, Accenture. And for ISO27001 most of IT networking company also could offer this standard consultation.
Do you have any other opinion with this comparison?
Others referrence:
ISACA: Aligning COBIT, ITIL and ISO 17799 for Business Benefit
Download Hundreds of Complimentary Industry Resources
Get hundreds of popular Industry magazines, white papers, webinars, podcasts, and more; all available at no cost to you. With more than 600 complimentary offers, you'll find plenty of titles to suit your professional interests and needs. Click Here and Sign up today!
Source : http://www.securityprocedure.com/
WikiLeaks Cable about Chinese Hacking of U.S. Networks
 We know it's prevalent, but there's some new information:
We know it's prevalent, but there's some new information:Secret U.S. State Department cables, obtained by WikiLeaks and made available to Reuters by a third party, trace systems breaches -- colorfully code-named "Byzantine Hades" by U.S. investigators -- to the Chinese military. An April 2009 cable even pinpoints the attacks to a specific unit of China's People's Liberation Army.
Privately, U.S. officials have long suspected that the Chinese government and in particular the military was behind the cyber-attacks. What was never disclosed publicly, until now, was evidence.
U.S. efforts to halt Byzantine Hades hacks are ongoing, according to four sources familiar with investigations. In the April 2009 cable, officials in the State Department's Cyber Threat Analysis Division noted that several Chinese-registered Web sites were "involved in Byzantine Hades intrusion activity in 2006."
The sites were registered in the city of Chengdu, the capital of Sichuan Province in central China, according to the cable. A person named Chen Xingpeng set up the sites using the "precise" postal code in Chengdu used by the People's Liberation Army Chengdu Province First Technical Reconnaissance Bureau (TRB), an electronic espionage unit of the Chinese military. "Much of the intrusion activity traced to Chengdu is similar in tactics, techniques and procedures to (Byzantine Hades) activity attributed to other" electronic spying units of the People's Liberation Army, the cable says.
[...]
What is known is the extent to which Chinese hackers use "spear-phishing" as their preferred tactic to get inside otherwise forbidden networks. Compromised email accounts are the easiest way to launch spear-phish because the hackers can send the messages to entire contact lists.
The tactic is so prevalent, and so successful, that "we have given up on the idea we can keep our networks pristine," says Stewart Baker, a former senior cyber-security official at the U.S. Department of Homeland Security and National Security Agency. It's safer, government and private experts say, to assume the worst -- that any network is vulnerable.
Two former national security officials involved in cyber-investigations told Reuters that Chinese intelligence and military units, and affiliated private hacker groups, actively engage in "target development" for spear-phish attacks by combing the Internet for details about U.S. government and commercial employees' job descriptions, networks of associates, and even the way they sign their emails -- such as U.S. military personnel's use of "V/R," which stands for "Very Respectfully" or "Virtual Regards."
The spear-phish are "the dominant attack vector. They work. They're getting better. It's just hard to stop," says Gregory J. Rattray, a partner at cyber-security consulting firm Delta Risk and a former director for cyber-security on the National Security Council.
Spear-phish are used in most Byzantine Hades intrusions, according to a review of State Department cables by Reuters. But Byzantine Hades is itself categorized into at least three specific parts known as "Byzantine Anchor," "Byzantine Candor," and "Byzantine Foothold." A source close to the matter says the sub-codenames refer to intrusions which use common tactics and malicious code to extract data.
A State Department cable made public by WikiLeaks last December highlights the severity of the spear-phish problem. "Since 2002, (U.S. government) organizations have been targeted with social-engineering online attacks" which succeeded in "gaining access to hundreds of (U.S. government) and cleared defense contractor systems," the cable said. The emails were aimed at the U.S. Army, the Departments of Defense, State and Energy, other government entities and commercial companies.
By the way, reading this blog entry might be illegal under the U.S. Espionage Act:
Dear Americans: If you are not "authorized" personnel, but you have read, written about, commented upon, tweeted, spread links by "liking" on Facebook, shared by email, or otherwise discussed "classified" information disclosed from WikiLeaks, you could be implicated for crimes under the U.S. Espionage Act -- or so warns a legal expert who said the U.S. Espionage Act could make "felons of us all."
As the U.S. Justice Department works on a legal case against WikiLeak's Julian Assange for his role in helping publish 250,000 classified U.S. diplomatic cables, authorities are leaning toward charging Assange with spying under the Espionage Act of 1917. Legal experts warn that if there is an indictment under the Espionage Act, then any citizen who has discussed or accessed "classified" information can be arrested on "national security" grounds.
Maybe I should have warned you at the top of this post.
Source : http://www.schneier.com/
Subscribe to:
Posts (Atom)


