Reuters reports that a new Brown University Study on the cost to the United States of the War on Terror has concluded that as many as a quarter million people have died as a direct result of bombs and bullets and that the final bill for waging war will be at least $3,700,000,000,000.
That $3.7 trillion, incredibly, is more than the entire annual gross domestic product of Germany, the world’s fourth-largest economy. It is more than the combined GDP of Great Britain and Canada, or the combined GDP of South Korea, the Netherlands, Switzerland, Sweden, Argentina, South Africa and Israel. You get the point.
It is far, far more than the $1 trillion President Barack Obama has cited as justification for withdrawing our troops from Afghanistan. According to the Brown study, titled “Costs of War,” the US has already spent between $2.3 and $2.7 trillion waging war since al-Qaeda attacked New York and Washington, DC on September 11, 2001.
Those attacks, by the way, exceeded Osama bin Laden’s wildest expectations, killing 2,995 people and causing $50- $100 billion in economic damage– and they cost no more than $500,000.
But what’s even more important is the human toll of this seemingly endless war against terrorism, a tactic that will never be eradicated as long as there disaffected and economically disadvantaged people on this planet. For every person killed by al-Qaeda on 9/11, 73 have been killed since. The Brown study measured only those killed directly by bombs and bullets as a result of the War on Terror. That number is between 224,000 and 258,000– the population of the entire city of Orlando, Florida, with 125,000 civilians dying in Iraq alone. And again, the study did not calculate those who have died from lack of health care, clean water and food resulting from the war. It did, however, count 365,000 wounded and 7.8 million– the population of the entire country of Switzerland or the combined populations of the states of New Hampshire, Idaho, West Virginia and Kansas– displaced persons.
These numbers, of course, will only continue to grow as the war drags on. And what’s often overlooked is the cost of taking care of the veterans who have served in Iraq and/or Afghanistan. To date, according to the Brown study, nearly half of the 1.25 million War on Terror vets have made health or disability claims, totaling some $32.6 billion. Over the next 40 years, those costs will soar to as high as $934 billion.
Another $401 billion has been spent since 9/11 on Homeland Security. Add another $185 billion in accumulated interest on the debt incurred from borrowing huge sums of money to finance the war. Then there’s the $74 billion spent on war-related foreign aid. Projected war-related spending though the year 2020 adds another $453 billion to the tab.
02 July 2011
28 June 2011
U.S. Soldiers forge new friendships in Indonesia
By Sgt. 1st Class Frank L. Marquez, 106th Public Affairs Detachment
BANDUNG, Indonesia (June 28, 2010) -- "What we leave behind will have a positive lasting impact," said Col. Tony Diaz, the U.S. commander for this year's fourth annual Garuda Shield 2010, which drew to a close June 22.
The exercise ended with a ceremony at Indonesia's Infantry Training Center, in the District of Cipatat, with U.S. Army Pacific Commander Lt. Gen. Benjamin R. Mixon and Lt. Gen. Budiman, the Training and Doctrine Commander for the Indonesian Army.
Garuda Shield 2010 hosted five other nations including Bangladesh, Brunei, Thailand, the Philippines, and Nepal in peacekeeping training for U.N. recognition, which encompassed role playing by senior leaders in a command post exercise, and security controls practiced by the nations' various armed forces in the field training exercise.
"Exercises like Garuda Shield better prepare us to address both traditional dilemmas and unconventional threats that transcend national borders," said Mixon, in explaining the purpose for the training. "Indonesia is a key partner nation that is taking an increasing role as a regional leader, and its armed forces continue to support ongoing peacekeeping efforts throughout the world."
Indonesia currently deploys thousands of troops to peacekeeping missions in Lebanon and the Congo.
Garuda Shield also provided humanitarian civic assistance, which benefited an estimated 250 households in the villages of Marga Mulya and Nyomplong. The project sites sit adjacent to the training center less than five miles away.
Engineers from the 797th Engineer Company -- 21 Reserve Soldiers from Guam -- joined with 89 Soldiers from the 9th and 3rd Engineering battalions of the TNI-AD to build a community center, baby clinic and open air amphitheatre. The HCA projects in 2009 are being used for baby care, dental care, and pre-school classes.
"We went out into the communities of Marga Mulya and Nyomplong to seek input," said Diaz, comparing the condition of the villages in Indonesia to the quality of life in the United States 100 years ago. "We asked what the communities needed. And leaders in the community would say that they would need such things as a place for women to wash laundry. So, we dug a well. In fact one of the village men dug the well by hand."
Ron O'Brien, the lead U.S. Army Pacific planner said that contracting allowed the engineers to build more than the projects that were planned before the exercise began in late May. Dollars were stretched twice as far as in previous years, according to O'Brien, so that the engineers were able to add a bath house, walkways and playgrounds to the list of projects already on the slate. "It's important for Hawaii to know what their Soldiers do," he said. "Those buildings will be there a long time."
Diaz added that the structures were made from Indonesian designs.
While the engineers built, the 9th Mission Support Command provided administrative support and the 29th Infantry Brigade Combat Team managed guidance on the lanes for the field exercise at the infantry training center.
"It's also important for people to know that an exercise of this magnitude requires funding from many sources to ensure success," O'Brien said. "USARPAC and the Pacific Command provided the bulk of the funding, while the Asia Pacific Regional Initiative funds paid for U.N. subject matter experts, which injected realism into the command post exercise."
As the nearly 160 U.S. Soldiers headed home, they took with them the memories of working together with their counterparts, and getting to know them as friends. Less than 24 hours before the closing ceremony, Mixon and other dignitaries had attended a dedication ceremony at the baby clinic.
Nearby, the Indonesian National Armed Forces or TNI were conducting a medical readiness exercise, at a clinic built in 2009. Tents were erected to shade more than a thousand village residents seeking treatment for their health concerns.
Diaz remarked that the structures from previous years continue to stand. He gestured to O'Brien and added that they had a chance to visit the year-old community center.
"The last time, we dropped by, the women were using it for a flea market," he said. "In fact, the mayor of the village had to schedule events; it got to be so popular. We see that it's being used as a preschool, for meetings, a wedding hall, and a recreation facility where they can play chess and checkers."
Ratih, 43, a resident in Marga Mulya, has a house that stands mere feet from the new community center. "Me and my family won't have to go far for meeting friends," she said smiling.
Capt. Alejandro Buniag, the commander for the 797th, pointed out that many of the infantry soldiers serving in the TNI-AD live in the same villages and have a vested interest in improving their communities. "So, there's a connection with the community," he said. "Even the people of the community know what it means. I watched as even the oldest man moved stones and materials to help us."
Siti Aminah, one of the leaders in the community, said its people feel obligated to help with manpower. She spent a lot of time knocking on doors, but didn't find any trouble finding help. "It's all volunteer-based," she said. "As part of the community, we assist with construction. People understand what it's for and gladly help."
The engineers shared that sense of community, bonding through the experience. They were laying the foundation of friendship, brick by brick, securing that friendship by pounding nails into wood frames. They talked, not only about different methods of construction, but of life and family.
Lt. Yudo, who headed the TNI's engineer contingent, said there are different options for doing things - some things were done by hand instead of using tools. And despite the language barriers, the Soldiers learned new handshakes and words in Bahasa, the various dialogues in Indonesia. Yudo said he relied on his experience of a year living and working in the Congo in 2006-07.
"We fixed the road, airfield and base camp," he said. "I find this exercise using the same kind of coordination."
With plans for an exercise in Bogor next year, the buzz from Soldiers was about coming back next year. Mixon addressed it at the closing ceremony. "Our countries continue to demonstrate the willingness to develop unified responses and bring together diverse governmental agencies and military capabilities to work closely on a range of shared interests," he said.
And the result is that many of the Soldiers look forward to seeing their friends again.
Photo note :
Lt. Gen. Benjamin Mixon, commander of U.S. Army Pacific, and Lt. Gen. Budiman, Training and Doctrine commander for the Indonesian National Armed Forces, review the troops at the closing ceremony of Operation Garuda Shield 2010, a humanitarian and peacekeeping training exercise. Background : Bangladesh, Brunei, Thailand, the Philippines and Nepal Armed Forces.
Link : http://www.army.mil/media/135198/
BANDUNG, Indonesia (June 28, 2010) -- "What we leave behind will have a positive lasting impact," said Col. Tony Diaz, the U.S. commander for this year's fourth annual Garuda Shield 2010, which drew to a close June 22.
The exercise ended with a ceremony at Indonesia's Infantry Training Center, in the District of Cipatat, with U.S. Army Pacific Commander Lt. Gen. Benjamin R. Mixon and Lt. Gen. Budiman, the Training and Doctrine Commander for the Indonesian Army.
Garuda Shield 2010 hosted five other nations including Bangladesh, Brunei, Thailand, the Philippines, and Nepal in peacekeeping training for U.N. recognition, which encompassed role playing by senior leaders in a command post exercise, and security controls practiced by the nations' various armed forces in the field training exercise.
"Exercises like Garuda Shield better prepare us to address both traditional dilemmas and unconventional threats that transcend national borders," said Mixon, in explaining the purpose for the training. "Indonesia is a key partner nation that is taking an increasing role as a regional leader, and its armed forces continue to support ongoing peacekeeping efforts throughout the world."
Indonesia currently deploys thousands of troops to peacekeeping missions in Lebanon and the Congo.
Garuda Shield also provided humanitarian civic assistance, which benefited an estimated 250 households in the villages of Marga Mulya and Nyomplong. The project sites sit adjacent to the training center less than five miles away.
Engineers from the 797th Engineer Company -- 21 Reserve Soldiers from Guam -- joined with 89 Soldiers from the 9th and 3rd Engineering battalions of the TNI-AD to build a community center, baby clinic and open air amphitheatre. The HCA projects in 2009 are being used for baby care, dental care, and pre-school classes.
"We went out into the communities of Marga Mulya and Nyomplong to seek input," said Diaz, comparing the condition of the villages in Indonesia to the quality of life in the United States 100 years ago. "We asked what the communities needed. And leaders in the community would say that they would need such things as a place for women to wash laundry. So, we dug a well. In fact one of the village men dug the well by hand."
Ron O'Brien, the lead U.S. Army Pacific planner said that contracting allowed the engineers to build more than the projects that were planned before the exercise began in late May. Dollars were stretched twice as far as in previous years, according to O'Brien, so that the engineers were able to add a bath house, walkways and playgrounds to the list of projects already on the slate. "It's important for Hawaii to know what their Soldiers do," he said. "Those buildings will be there a long time."
Diaz added that the structures were made from Indonesian designs.
While the engineers built, the 9th Mission Support Command provided administrative support and the 29th Infantry Brigade Combat Team managed guidance on the lanes for the field exercise at the infantry training center.
"It's also important for people to know that an exercise of this magnitude requires funding from many sources to ensure success," O'Brien said. "USARPAC and the Pacific Command provided the bulk of the funding, while the Asia Pacific Regional Initiative funds paid for U.N. subject matter experts, which injected realism into the command post exercise."
As the nearly 160 U.S. Soldiers headed home, they took with them the memories of working together with their counterparts, and getting to know them as friends. Less than 24 hours before the closing ceremony, Mixon and other dignitaries had attended a dedication ceremony at the baby clinic.
Nearby, the Indonesian National Armed Forces or TNI were conducting a medical readiness exercise, at a clinic built in 2009. Tents were erected to shade more than a thousand village residents seeking treatment for their health concerns.
Diaz remarked that the structures from previous years continue to stand. He gestured to O'Brien and added that they had a chance to visit the year-old community center.
"The last time, we dropped by, the women were using it for a flea market," he said. "In fact, the mayor of the village had to schedule events; it got to be so popular. We see that it's being used as a preschool, for meetings, a wedding hall, and a recreation facility where they can play chess and checkers."
Ratih, 43, a resident in Marga Mulya, has a house that stands mere feet from the new community center. "Me and my family won't have to go far for meeting friends," she said smiling.
Capt. Alejandro Buniag, the commander for the 797th, pointed out that many of the infantry soldiers serving in the TNI-AD live in the same villages and have a vested interest in improving their communities. "So, there's a connection with the community," he said. "Even the people of the community know what it means. I watched as even the oldest man moved stones and materials to help us."
Siti Aminah, one of the leaders in the community, said its people feel obligated to help with manpower. She spent a lot of time knocking on doors, but didn't find any trouble finding help. "It's all volunteer-based," she said. "As part of the community, we assist with construction. People understand what it's for and gladly help."
The engineers shared that sense of community, bonding through the experience. They were laying the foundation of friendship, brick by brick, securing that friendship by pounding nails into wood frames. They talked, not only about different methods of construction, but of life and family.
Lt. Yudo, who headed the TNI's engineer contingent, said there are different options for doing things - some things were done by hand instead of using tools. And despite the language barriers, the Soldiers learned new handshakes and words in Bahasa, the various dialogues in Indonesia. Yudo said he relied on his experience of a year living and working in the Congo in 2006-07.
"We fixed the road, airfield and base camp," he said. "I find this exercise using the same kind of coordination."
With plans for an exercise in Bogor next year, the buzz from Soldiers was about coming back next year. Mixon addressed it at the closing ceremony. "Our countries continue to demonstrate the willingness to develop unified responses and bring together diverse governmental agencies and military capabilities to work closely on a range of shared interests," he said.
And the result is that many of the Soldiers look forward to seeing their friends again.
Photo note :
Lt. Gen. Benjamin Mixon, commander of U.S. Army Pacific, and Lt. Gen. Budiman, Training and Doctrine commander for the Indonesian National Armed Forces, review the troops at the closing ceremony of Operation Garuda Shield 2010, a humanitarian and peacekeeping training exercise. Background : Bangladesh, Brunei, Thailand, the Philippines and Nepal Armed Forces.
Link : http://www.army.mil/media/135198/
15 June 2011
In US Army, the beret is out and the cap is back
WASHINGTON (AFP) – The US Army is abandoning the beret, after a failed 10-year experiment.
The black beret, which proved deeply unpopular with American soldiers, will be replaced by a patrol cap for everyday wear, US Army spokesman Colonel Tom Collins said Monday.
The move came after outgoing Army chief of staff, General Martin Dempsey, asked the army's sergeant major "to go out and talk to soldiers across the force and see what was on their minds," Collins told AFP.
"One of the things that soldiers consistently brought up was the desire to wear the patrol cap as part of their duty uniform," he said.
The beret will still be part of the Army's dress uniform, but will no longer be worn in the field as soldiers complained that it was impractical, he said.
"It does not have a visor and doesn't shield the sun, doesn't absorb sweat well," Collins said.
One soldier put it more bluntly.
"I hate wearing a wet sock on my head," Chief Warrant Officer Mark Vino, at Joint Base Lewis-McChord in Washington state, told the Army Times. "Plus it makes head/skin break out."
Before 2001, the black beret was associated with the elite Rangers special operations forces. Many Rangers resented the idea that the hat they had earned the right to wear had been assigned to the entire force.
The uniform change applies to 1.32 million soldiers -- including 566,473 active duty troops -- and goes into effect immediately. The new headwear comes with a lower price: a beret costs $11.90 while a patrol cap is only $6.50.
The decision does not affect units that have long worn berets as a mark of distinction, including the Rangers' black beret, Army special forces' green beret and Airborne's maroon version.
As part of the change, soldiers will have the option of having their name tags, rank and badges sewn on to their uniforms.
There also will be a new look for Army soldiers working at the Defense Department's headquarters at the Pentagon, with camouflage to be replaced with the more business-like dress uniform, Collins said.
"For soldiers serving in the Pentagon, we will transition to the dress uniform," starting in July, he said.
In the aftermath of the attacks of September 11, 2001, all the armed services started wearing combat uniforms in the Pentagon, to underscore the country's war-footing.
But Defense Secretary Robert Gates last year had his staff drop the combat uniforms, and some other offices in the Pentagon have returned to the dress uniform.
"Our perspective is that this is the corporate part of the Army," said Sergeant Major of the Army, Raymond Chandler, quoted on the US Army's website.
The black beret, which proved deeply unpopular with American soldiers, will be replaced by a patrol cap for everyday wear, US Army spokesman Colonel Tom Collins said Monday.
The move came after outgoing Army chief of staff, General Martin Dempsey, asked the army's sergeant major "to go out and talk to soldiers across the force and see what was on their minds," Collins told AFP.
"One of the things that soldiers consistently brought up was the desire to wear the patrol cap as part of their duty uniform," he said.
The beret will still be part of the Army's dress uniform, but will no longer be worn in the field as soldiers complained that it was impractical, he said.
"It does not have a visor and doesn't shield the sun, doesn't absorb sweat well," Collins said.
One soldier put it more bluntly.
"I hate wearing a wet sock on my head," Chief Warrant Officer Mark Vino, at Joint Base Lewis-McChord in Washington state, told the Army Times. "Plus it makes head/skin break out."
Before 2001, the black beret was associated with the elite Rangers special operations forces. Many Rangers resented the idea that the hat they had earned the right to wear had been assigned to the entire force.
The uniform change applies to 1.32 million soldiers -- including 566,473 active duty troops -- and goes into effect immediately. The new headwear comes with a lower price: a beret costs $11.90 while a patrol cap is only $6.50.
The decision does not affect units that have long worn berets as a mark of distinction, including the Rangers' black beret, Army special forces' green beret and Airborne's maroon version.
As part of the change, soldiers will have the option of having their name tags, rank and badges sewn on to their uniforms.
There also will be a new look for Army soldiers working at the Defense Department's headquarters at the Pentagon, with camouflage to be replaced with the more business-like dress uniform, Collins said.
"For soldiers serving in the Pentagon, we will transition to the dress uniform," starting in July, he said.
In the aftermath of the attacks of September 11, 2001, all the armed services started wearing combat uniforms in the Pentagon, to underscore the country's war-footing.
But Defense Secretary Robert Gates last year had his staff drop the combat uniforms, and some other offices in the Pentagon have returned to the dress uniform.
"Our perspective is that this is the corporate part of the Army," said Sergeant Major of the Army, Raymond Chandler, quoted on the US Army's website.
14 June 2011
U.S., Indonesia maintain a partnership of peace
By Sgt. 1st Class Frank L. Marquez
BANDUNG, Indonesia -- Continuing an era of cooperation, the Indonesian military hosted the opening ceremony of Garuda Shield 2010 on Thursday at the Tentara Nasional Indonesia (TNI) Infantry Training Center in the District of Cipatat.
Maj. Gen. Soenarko, commander of the infantry center, and Maj. Gen. Robert G.F. Lee, the adjutant general of Hawaii Army National Guard (HIARNG), greeted more than 1,100 military members at the hour-long ceremony. Representatives from Indonesia, Bangladesh, Brunei, Thailand, Nepal, Philippines and the United States stood in a mass formation while listening to welcoming remarks delivered by both Soenarko and Lee.
Garuda Shield began four years ago in Bogor with the goal of training various nations' militaries for United Nations peacekeeping missions. The objectives have not changed over the years with the exception of the Indonesians taking the lead on training. Their U.S. counterparts now give limited guidance.
"Each country has its own standard, which explains the reason for having a U.N. certification," Soenarko said. "The idea is to have one standard."
Indonesia is preparing to send an engineering company to Lebanon later this year. The Indonesians have been sending troops to Lebanon for year-long rotations since December 2006, according to Maj. Charles Carter, exercise coordinator. The Indonesians have also deployed engineers to the Congo.
"The objectives of this exercise show Indonesia's contribution for worldwide peace, and the solidarity between participating countries," Lee said. "The benefit of having exercises like Garuda Shield is the knowledge that we can work together when natural or other disasters strike."
As part of the exercise, staff officers from the Pacific Command, the HIARNG, USARPAC, and the TNI will form a brigade to test peace support and stability operations capabilities.
Other troops are in the middle of conducting a field training exercise to exchange UN standardized organizational tactics, techniques and procedures to improve tactical interoperability.
Meanwhile, engineers are working in Indonesia's rural communities to provide humanitarian civic actions (HCA). Every day scores of children mil about the construction sites to watch the progress. Engineer partners are making quick work of a baby clinic, community center and amphitheatre.
"As the executive of the mission, without forgetting the peacekeeping and field training aspect, I strongly emphasize the lasting impression those kids will have of the U.S.," said Exercise Commander Col. Tony Diaz. "That's priceless. It's beneficial when those communities see our soldiers working next to their soldiers."
The HCA work sites represent how the U.S. and Indonesian military-to-military ties have improved greatly in the last five years, and hold the promise of continued improvement in the years to come, according to organizers. There remain some minor challenges. Lee described one of those hurdles as having the appropriate mindset. "First, countries are asked to defend their own nations," he said. "But they are also asked to be diplomats. Therefore, we must involve many more nations in our efforts which would be a key to circumventing world conflicts."
Sgt. Rick Domec of the HIARNG met that challenge as he arrived in Indonesia. He discovered that U.N. standards apply different rules of engagement. He and Soldiers from C Troop, 299 Cav (Recon Surveillance Target Acquisition), have been observing the various tactics at the field training exercise adjacent to the TNI Training Center.
"We just returned from a deployment in Kuwait last August and September. We were running convoy operations through Iraq to as far as Mosul," he said. "There, we had to constantly be alert. But with the U.N., we don't have to look at everyone as a threat. We look at them as friends, and we are asked to identify ourselves as U.N. peacekeepers."
As Indonesia grows more confident in its training role, it is believed that the same will happen with other nations. "In three years, I've seen the Indonesian military progress. This is their exercise now," Diaz said. "We came here to provide support and guidance, but they run it. They plan it. They execute it. They are on a par with any national military that I've been associated with in my 29 years.
Diaz added that "hopefully with U.N. training, other nations will accept a larger role as their forces become more professional with access to training like Garuda Shield 2010, and they develop military doctrine modeled after our education system - the Command and Staff College, and Army War College. Those countries can then become our strategic partners."
(Spc. Emerson Marcus, 106th Public Affairs Detachment, contributed to this report.)
Photo Note :
BANDUNG, Indonesia -- Col. Nono Mulyono, Maj. Gen. Soenarko, and Maj. Gen. Robert G.F. Lee review the more than 1,100 troops representing six nations standing in formation at the Opening Ceremony for Garuda Shield 2010.
Link : http://www.army.mil/article/40837/
BANDUNG, Indonesia -- Continuing an era of cooperation, the Indonesian military hosted the opening ceremony of Garuda Shield 2010 on Thursday at the Tentara Nasional Indonesia (TNI) Infantry Training Center in the District of Cipatat.
Maj. Gen. Soenarko, commander of the infantry center, and Maj. Gen. Robert G.F. Lee, the adjutant general of Hawaii Army National Guard (HIARNG), greeted more than 1,100 military members at the hour-long ceremony. Representatives from Indonesia, Bangladesh, Brunei, Thailand, Nepal, Philippines and the United States stood in a mass formation while listening to welcoming remarks delivered by both Soenarko and Lee.
Garuda Shield began four years ago in Bogor with the goal of training various nations' militaries for United Nations peacekeeping missions. The objectives have not changed over the years with the exception of the Indonesians taking the lead on training. Their U.S. counterparts now give limited guidance.
"Each country has its own standard, which explains the reason for having a U.N. certification," Soenarko said. "The idea is to have one standard."
Indonesia is preparing to send an engineering company to Lebanon later this year. The Indonesians have been sending troops to Lebanon for year-long rotations since December 2006, according to Maj. Charles Carter, exercise coordinator. The Indonesians have also deployed engineers to the Congo.
"The objectives of this exercise show Indonesia's contribution for worldwide peace, and the solidarity between participating countries," Lee said. "The benefit of having exercises like Garuda Shield is the knowledge that we can work together when natural or other disasters strike."
As part of the exercise, staff officers from the Pacific Command, the HIARNG, USARPAC, and the TNI will form a brigade to test peace support and stability operations capabilities.
Other troops are in the middle of conducting a field training exercise to exchange UN standardized organizational tactics, techniques and procedures to improve tactical interoperability.
Meanwhile, engineers are working in Indonesia's rural communities to provide humanitarian civic actions (HCA). Every day scores of children mil about the construction sites to watch the progress. Engineer partners are making quick work of a baby clinic, community center and amphitheatre.
"As the executive of the mission, without forgetting the peacekeeping and field training aspect, I strongly emphasize the lasting impression those kids will have of the U.S.," said Exercise Commander Col. Tony Diaz. "That's priceless. It's beneficial when those communities see our soldiers working next to their soldiers."
The HCA work sites represent how the U.S. and Indonesian military-to-military ties have improved greatly in the last five years, and hold the promise of continued improvement in the years to come, according to organizers. There remain some minor challenges. Lee described one of those hurdles as having the appropriate mindset. "First, countries are asked to defend their own nations," he said. "But they are also asked to be diplomats. Therefore, we must involve many more nations in our efforts which would be a key to circumventing world conflicts."
Sgt. Rick Domec of the HIARNG met that challenge as he arrived in Indonesia. He discovered that U.N. standards apply different rules of engagement. He and Soldiers from C Troop, 299 Cav (Recon Surveillance Target Acquisition), have been observing the various tactics at the field training exercise adjacent to the TNI Training Center.
"We just returned from a deployment in Kuwait last August and September. We were running convoy operations through Iraq to as far as Mosul," he said. "There, we had to constantly be alert. But with the U.N., we don't have to look at everyone as a threat. We look at them as friends, and we are asked to identify ourselves as U.N. peacekeepers."
As Indonesia grows more confident in its training role, it is believed that the same will happen with other nations. "In three years, I've seen the Indonesian military progress. This is their exercise now," Diaz said. "We came here to provide support and guidance, but they run it. They plan it. They execute it. They are on a par with any national military that I've been associated with in my 29 years.
Diaz added that "hopefully with U.N. training, other nations will accept a larger role as their forces become more professional with access to training like Garuda Shield 2010, and they develop military doctrine modeled after our education system - the Command and Staff College, and Army War College. Those countries can then become our strategic partners."
(Spc. Emerson Marcus, 106th Public Affairs Detachment, contributed to this report.)
Photo Note :
BANDUNG, Indonesia -- Col. Nono Mulyono, Maj. Gen. Soenarko, and Maj. Gen. Robert G.F. Lee review the more than 1,100 troops representing six nations standing in formation at the Opening Ceremony for Garuda Shield 2010.
Link : http://www.army.mil/article/40837/
12 June 2011
US, Indonesia partner for Exercise Garuda Shield 2011
By Capt. Christina Douglas, 9th Mission Support Command
BOGOR, Indonesia " Hundreds of U.S. and Indonesian Soldiers gathered to participate in the opening ceremony of an annual bilateral exercise, today, at the Tentara Nasional Indonesia (TNI-Indonesian Armed Forces) Engineer Training Center of Army Education and Training Command, Pusdikzi.
Sponsored by U.S. Army, Pacific and hosted by the Indonesian Armed Forces, Exercise Garuda Shield is the latest in a continuing series of rigorous, multi-faceted exercises designed to promote regional peace and security.
This year’s exercise is comprised of three main components: a command post exercise, a field training exercise and a humanitarian civic action project.
Productive team-building efforts and staff processes for resolving complex security situations will be the focus of the CPX. Soldiers of the 9th MSC and Hawaii Army National Guard’s 29th Infantry Brigade Combat Team will serve as members of division, brigade and battalion staff, working closely with their TNI counterparts.
The FTX, led by the Asia Pacific Counter Improvised Explosive Device Fusion Center, will consist of academics and small unit training designed to counter IEDs. U.S. Soldiers will train approximately 240 Indonesian Soldiers how to identify and react to potentially hazardous situations.
Additionally, Hawaii-based Army Reservists of the 871st Engineer Detachment, 411th Engineer Battalion, 9th MSC, will partner with their Indonesian counterparts to complete a humanitarian civic action project. This intense engineering effort will result in the establishment of a large, modern community services building and public market in a rural district.
Participants from U.S. and Indonesia will further strengthen their relationships by competing in sporting events and enjoying cultural activities.
During the opening ceremony, Brig. Gen. Michele G. Compton, the commanding general of the 9th MSC, welcomed the troops and described the importance of the regionally significant training event.
“Garuda Shield is an opportunity for the Indonesian Army and the United States Army to come together in a learning environment to share experiences and lessons learned with each other. Of equal importance during this exercise, is the opportunity to form and maintain close friendships and also to gain an enduring appreciation of each other’s customs,” said Compton.
Brig. Gen. Mulyono, the training director for the TNI Training and Doctrine Command said the exercise is, “expected to further strengthen the professionalism of the Soldiers as well as to deepen and strengthen cooperation between the Indonesian Army and USARPAC, which is based on mutual respect.”
Exercise Garuda Shield 2011 is slated to conclude June 22.
Photo Note :
U.S., Indonesia kick off bilateral exercise
BOGOR, Indonesia – Brig. Gen. Michele G. Compton, the commanding general of the 9th Mission Support Command, and Brig. Gen. Mulyono, the training director for the Tentara Nasional Indonesia (TNI-Indonesian Armed Forces) Training and Doctrine Command.
Link : http://www.army.mil/article/59478/
BOGOR, Indonesia " Hundreds of U.S. and Indonesian Soldiers gathered to participate in the opening ceremony of an annual bilateral exercise, today, at the Tentara Nasional Indonesia (TNI-Indonesian Armed Forces) Engineer Training Center of Army Education and Training Command, Pusdikzi.
Sponsored by U.S. Army, Pacific and hosted by the Indonesian Armed Forces, Exercise Garuda Shield is the latest in a continuing series of rigorous, multi-faceted exercises designed to promote regional peace and security.
This year’s exercise is comprised of three main components: a command post exercise, a field training exercise and a humanitarian civic action project.
Productive team-building efforts and staff processes for resolving complex security situations will be the focus of the CPX. Soldiers of the 9th MSC and Hawaii Army National Guard’s 29th Infantry Brigade Combat Team will serve as members of division, brigade and battalion staff, working closely with their TNI counterparts.
The FTX, led by the Asia Pacific Counter Improvised Explosive Device Fusion Center, will consist of academics and small unit training designed to counter IEDs. U.S. Soldiers will train approximately 240 Indonesian Soldiers how to identify and react to potentially hazardous situations.
Additionally, Hawaii-based Army Reservists of the 871st Engineer Detachment, 411th Engineer Battalion, 9th MSC, will partner with their Indonesian counterparts to complete a humanitarian civic action project. This intense engineering effort will result in the establishment of a large, modern community services building and public market in a rural district.
Participants from U.S. and Indonesia will further strengthen their relationships by competing in sporting events and enjoying cultural activities.
During the opening ceremony, Brig. Gen. Michele G. Compton, the commanding general of the 9th MSC, welcomed the troops and described the importance of the regionally significant training event.
“Garuda Shield is an opportunity for the Indonesian Army and the United States Army to come together in a learning environment to share experiences and lessons learned with each other. Of equal importance during this exercise, is the opportunity to form and maintain close friendships and also to gain an enduring appreciation of each other’s customs,” said Compton.
Brig. Gen. Mulyono, the training director for the TNI Training and Doctrine Command said the exercise is, “expected to further strengthen the professionalism of the Soldiers as well as to deepen and strengthen cooperation between the Indonesian Army and USARPAC, which is based on mutual respect.”
Exercise Garuda Shield 2011 is slated to conclude June 22.
Photo Note :
U.S., Indonesia kick off bilateral exercise
BOGOR, Indonesia – Brig. Gen. Michele G. Compton, the commanding general of the 9th Mission Support Command, and Brig. Gen. Mulyono, the training director for the Tentara Nasional Indonesia (TNI-Indonesian Armed Forces) Training and Doctrine Command.
Link : http://www.army.mil/article/59478/
24 May 2011
Setting Up Your POP3 Email Address in Microsoft Outlook
If you want to access email batan.go.id domain, please follow instructions below.
For Microsoft Outlook users :
Incoming Mail (POP3) : mail.batan.go.id
Outgoing mail (SMTP) : mail.batan.go.id
Server port number for SMTP: 25
This server requires a secure connection (SSL) : enable
Server port number for POP3: 995
This server requires a secure connection (SSL) : enable
For Thunderbirds user :
Incoming : mail.batan.go.id, POP, 110, STARTTLS
Outgoing : mail.batan.go.id, SMTP, 25, STARTTLS
For Mail in Mac OS :
Click menu Mail then Preferences
Type = POP or IMAP
incoming mail server = mail.batan.go.id
SMTP
Outgoing mail server = mail.batan.go.id
For Microsoft Outlook users :
Incoming Mail (POP3) : mail.batan.go.id
Outgoing mail (SMTP) : mail.batan.go.id
Server port number for SMTP: 25
This server requires a secure connection (SSL) : enable
Server port number for POP3: 995
This server requires a secure connection (SSL) : enable
For Thunderbirds user :
Incoming : mail.batan.go.id, POP, 110, STARTTLS
Outgoing : mail.batan.go.id, SMTP, 25, STARTTLS
For Mail in Mac OS :
Click menu Mail then Preferences
Type = POP or IMAP
incoming mail server = mail.batan.go.id
SMTP
Outgoing mail server = mail.batan.go.id
19 May 2011
Comparison Movie Recording between DSLR and Handycam
In this article, I'll compare the movie-making between DSLR Camera and Handycam. I used DSLR Camera Canon EOS 550D and handycam Sony DCR SR-45.
Video recording with DSLR Camera Canon EOS 550D
Movie rec. size = 1920 x 1080
36,2 MB = 6 sec -> 6,03 MB per sec
45,9 MB = 8 sec -> 5,74 MB per sec
36,0 MB = 6 sec -> 6,00 MB per sec
Error message : Movie recording has been stopped automatically
Movie rec. size = 1280 x 720
33.5 MB = 6 sec -> 5,58 MB per sec
35.2 MB = 6 sec -> 5.87 MB per sec
30.1 MB = 5 sec -> 6,02 MB per sec
Error message : Movie recording has been stopped automatically
Movie rec. size = 640 x 480
59.8 MB = 22 sec -> 2.71 MB per sec
80.5 MB = 31 sec -> 2,60 MB per sec
27,9 MB = 10 sec -> 2,79 MB per sec
No error message.
Canon EOS 550D has file format MVI_xxxx.MOV dan MVI_xxxx.THM
Video recording with Handycam Sony DCR SR-45
Movie rec. size ?
15,0 MB = 19 sec -> 0,79 MB per sec
19,5 MB = 23 sec -> 0,85 MB per sec
69,0 MB = 82 sec -> 0,84 MB per sec
File format : M2Uxxxxx.MPG
Video recording with DSLR Camera Canon EOS 550D
Movie rec. size = 1920 x 1080
36,2 MB = 6 sec -> 6,03 MB per sec
45,9 MB = 8 sec -> 5,74 MB per sec
36,0 MB = 6 sec -> 6,00 MB per sec
Error message : Movie recording has been stopped automatically
Movie rec. size = 1280 x 720
33.5 MB = 6 sec -> 5,58 MB per sec
35.2 MB = 6 sec -> 5.87 MB per sec
30.1 MB = 5 sec -> 6,02 MB per sec
Error message : Movie recording has been stopped automatically
Movie rec. size = 640 x 480
59.8 MB = 22 sec -> 2.71 MB per sec
80.5 MB = 31 sec -> 2,60 MB per sec
27,9 MB = 10 sec -> 2,79 MB per sec
No error message.
Canon EOS 550D has file format MVI_xxxx.MOV dan MVI_xxxx.THM
Video recording with Handycam Sony DCR SR-45
Movie rec. size ?
15,0 MB = 19 sec -> 0,79 MB per sec
19,5 MB = 23 sec -> 0,85 MB per sec
69,0 MB = 82 sec -> 0,84 MB per sec
File format : M2Uxxxxx.MPG
18 May 2011
How To Install Adobe Acrobat Reader in Fedora 13 and Previous Versions
This brief tutorial will show you how to easily install Adobe Acrobat PDF Reader in Fedora 13, codenamed Goddard. There are many ways to install Adobe Reader in Fedora, but this method is the easiest. After installing you will be able to open PDF documents with Adobe PDF Reader.
See more : http://www.liberiangeek.net/2010/06/how-to-install-adobe-acrobat-reader-in-fedora-13-and-previous-versions/
See more : http://www.liberiangeek.net/2010/06/how-to-install-adobe-acrobat-reader-in-fedora-13-and-previous-versions/
15 May 2011
Computer Security Devices
To protect your network computer, you can use devices such as IPS HP Tipping Point S110, BlueCoat Proxy SG/ProxyAV, Citrix NetScaler, Tufin T-500, Riverbed SteelHead. The function and position on LAN of every device, is different.
The AppDV security solution is just one part of our HP TippingPoint comprehensive application security portfolio comprised of our Intrusion Prevention System (IPS), Security Management System (SMS), and hundreds of Digital Vaccines developed by DVLabs - all designed to help you manage and protect your vulnerable applications and your network from exploits and attacks.
The Blue Coat ProxySG appliance represents the latest in perimeter defense for securing and controlling Web-based content and applications. The Blue Coat ProxySG was designed to integrate protection and control functions for Internet and intranet traffic without sacrificing performance and employee productivity.
Citrix© NetScaler© is an all-in-one Web application delivery solution that makes applications run five times better by ensuring application availability through advanced L4-7 traffic management, by increasing security with an integrated application firewall and by substantially lowering costs by offloading servers. This reduces TCO, optimizes the user experience and makes sure that applications are always available. See more.
Tufin's SecureTrack provides configuration change monitoring, reporting, and alerting features specifically for corporate firewalls. Check Point (NG FP3+), Cisco (PIX, ASA, FWSM, IOS Routers), Juniper (ScreenOS), and soon Fortinet (FortiGate) firewalls are all supported. (How about MikroTik RouterBoard?)
The product is deployed on a central Red Hat (Enterprise Linux, CentOS) server. For Check Point firewalls, the product tracks all changes made by admins (watching for policy saves or installs) logged onto a Check Point SmartDashboard or Provider-1 GUI. When such changes are noted, the central server uses OPSEC to retrieve the policy, storing it in its own internal DB for subsequent analysis. For other supported firewalls, the product periodically logs into the firewall via SSH, retrieving the firewall's policies and ACLs and translating them into the product's internal XML rule base format. See more.
Riverbed Technology positions itself as being in the business of providing performance improvements to networked environments. Riverbed's WAN optimization products, both appliance-based and virtual, are branded under the product name Steelhead. The company differentiates itself in the market in part based on the relationships that it has with key technology partners, including Microsoft, EMC, HP, IBM and VMware. See more.
Price List
The AppDV security solution is just one part of our HP TippingPoint comprehensive application security portfolio comprised of our Intrusion Prevention System (IPS), Security Management System (SMS), and hundreds of Digital Vaccines developed by DVLabs - all designed to help you manage and protect your vulnerable applications and your network from exploits and attacks.
The Blue Coat ProxySG appliance represents the latest in perimeter defense for securing and controlling Web-based content and applications. The Blue Coat ProxySG was designed to integrate protection and control functions for Internet and intranet traffic without sacrificing performance and employee productivity.
Citrix© NetScaler© is an all-in-one Web application delivery solution that makes applications run five times better by ensuring application availability through advanced L4-7 traffic management, by increasing security with an integrated application firewall and by substantially lowering costs by offloading servers. This reduces TCO, optimizes the user experience and makes sure that applications are always available. See more.
Tufin's SecureTrack provides configuration change monitoring, reporting, and alerting features specifically for corporate firewalls. Check Point (NG FP3+), Cisco (PIX, ASA, FWSM, IOS Routers), Juniper (ScreenOS), and soon Fortinet (FortiGate) firewalls are all supported. (How about MikroTik RouterBoard?)
The product is deployed on a central Red Hat (Enterprise Linux, CentOS) server. For Check Point firewalls, the product tracks all changes made by admins (watching for policy saves or installs) logged onto a Check Point SmartDashboard or Provider-1 GUI. When such changes are noted, the central server uses OPSEC to retrieve the policy, storing it in its own internal DB for subsequent analysis. For other supported firewalls, the product periodically logs into the firewall via SSH, retrieving the firewall's policies and ACLs and translating them into the product's internal XML rule base format. See more.
Riverbed Technology positions itself as being in the business of providing performance improvements to networked environments. Riverbed's WAN optimization products, both appliance-based and virtual, are branded under the product name Steelhead. The company differentiates itself in the market in part based on the relationships that it has with key technology partners, including Microsoft, EMC, HP, IBM and VMware. See more.
Price List
- HP Tipping Point S110, US$9,289.99
- Blue Coat ProxySG 300 Series SG300-25 - security appliance, USD $8,780.99
- Citrix Netscaler NS 7000 Security Access Gateway, US $3,999.99
- Tufin T-500 Appliance (Up to 100 firewalls, Quad-Core Intel® Xeon®, 8GB RAM, 1U, Dual PSU, RAID, 1-Year Support and Advanced Replacement Program Warranty), US$5,300
- Riverbed Steelhead 1050-L (SHA-01050-L) with 4 onboard GbE bypass ports (800 conn/6Mbps), US$12,972. Can use single Steelhead? Or need a pair?
14 May 2011
Anything about MikroTik Hotspot
Articles related with Mikrotik hotspot such as :
HotSpot Gateway Documentation
Manual:IP/Hotspot
http://www.settingmikrotik.com/
Step by Step Setup Hotspot dengan Halaman Login di Mikrotik Router OS
Konfigurasi Hotspot Mikrotik
How to Setup Your Own Hotspot with MIKROTIK routers
Mikrotik Hotspot dan User Manager
Cara hack hotspot mikrotik
Mikrotik Hotspot Hacking
Setting Radius dan hotspot Mikrotik
HotSpot Gateway Documentation
Manual:IP/Hotspot
http://www.settingmikrotik.com/
Step by Step Setup Hotspot dengan Halaman Login di Mikrotik Router OS
Konfigurasi Hotspot Mikrotik
How to Setup Your Own Hotspot with MIKROTIK routers
Mikrotik Hotspot dan User Manager
Cara hack hotspot mikrotik
Mikrotik Hotspot Hacking
Setting Radius dan hotspot Mikrotik
10 May 2011
The Meaning of MikroTik Log Messages on Linux Server
This is example of log messages from MikroTik. I am trying to understand the causes of these logs and the rule where the Mikrotik that produce it. I tried to group them in the same time sequence.
May 9 23:43:46 183.91.67.2 KPB Unknown(81) = 00-00-00-42-50-41-2D-41-47-2D-50-43
May 9 23:43:46 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 9 23:43:46 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific
May 9 23:43:46 KPB dhcp_bsdm sending ack with id 1548336385 to 255.255.255.255
May 9 23:43:46 183.91.67.2 KPB flags = broadcast
May 9 23:43:46 183.91.67.2 KPB ciaddr = 0.0.0.0
May 9 23:43:46 183.91.67.2 KPB yiaddr = 192.168.2.85
May 9 23:43:46 183.91.67.2 KPB siaddr = 192.168.2.1
May 9 23:43:46 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 9 23:43:46 183.91.67.2 KPB Msg-Type = ack
May 9 23:43:46 183.91.67.2 KPB Server-Id = 192.168.2.1
May 9 23:43:46 183.91.67.2 KPB Address-Time = 31536000
May 9 23:43:46 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 9 23:43:46 183.91.67.2 KPB Router = 192.168.2.1
May 9 23:43:46 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 9 23:58:08 KPB dhcp_bu received inform with id 420795606 from 192.168.1.246
May 9 23:58:08 183.91.67.2 KPB Msg-Type = inform
May 9 23:58:08 183.91.67.2 KPB Client-Id = 01-00-50-8D-9F-48-F9
May 9 23:58:08 183.91.67.2 KPB Host-Name = "Windows7-PC"
May 9 23:58:08 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 9 23:58:08 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific,Unknown(252)
May 9 23:58:08 KPB dhcp_bu sending ack with id 420795606 to 255.255.255.255
May 9 23:58:08 183.91.67.2 KPB flags = broadcast
May 9 23:58:08 183.91.67.2 KPB ciaddr = 192.168.1.246
May 9 23:58:08 183.91.67.2 KPB siaddr = 192.168.1.129
May 9 23:58:08 183.91.67.2 KPB chaddr = 00:50:8D:9F:48:F9
May 9 23:58:08 183.91.67.2 KPB Msg-Type = ack
May 9 23:58:08 183.91.67.2 KPB Server-Id = 192.168.1.129
May 9 23:58:08 183.91.67.2 KPB Subnet-Mask = 255.255.255.128
May 9 23:58:08 183.91.67.2 KPB Router = 192.168.1.129
May 9 23:58:08 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:14:15 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:14:15 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:14:15 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:18:50 KPB dhcp_bsdm received request with id 2652037990 from 0.0.0.0
May 10 00:18:50 183.91.67.2 KPB flags = broadcast
May 10 00:18:50 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:18:50 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:18:50 183.91.67.2 KPB Msg-Type = request
May 10 00:18:50 183.91.67.2 KPB Client-Id = 01-00-15-F2-82-D9-39
May 10 00:18:50 183.91.67.2 KPB Address-Request = 192.168.2.85
May 10 00:18:50 183.91.67.2 KPB Host-Name = "BPA-AG-PC"
May 10 00:18:50 183.91.67.2 KPB Unknown(81) = 00-00-00-42-50-41-2D-41-47-2D-50-43
May 10 00:18:50 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 10 00:18:50 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific
May 10 00:18:50 KPB dhcp_bsdm sending ack with id 2652037990 to 255.255.255.255
May 10 00:18:50 183.91.67.2 KPB flags = broadcast
May 10 00:18:50 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:18:50 183.91.67.2 KPB yiaddr = 192.168.2.85
May 10 00:18:50 183.91.67.2 KPB siaddr = 192.168.2.1
May 10 00:18:50 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:18:50 183.91.67.2 KPB Msg-Type = ack
May 10 00:18:50 183.91.67.2 KPB Server-Id = 192.168.2.1
May 10 00:18:50 183.91.67.2 KPB Address-Time = 31536000
May 10 00:18:50 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:18:50 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:18:50 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:31:37 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:31:37 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:31:37 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:31:48 KPB dhcp_bsdm received request with id 3594588014 from 0.0.0.0
May 10 00:31:48 183.91.67.2 KPB flags = broadcast
May 10 00:31:48 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:31:48 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:31:48 183.91.67.2 KPB Msg-Type = request
May 10 00:31:48 183.91.67.2 KPB Client-Id = 01-00-15-F2-82-D9-39
May 10 00:31:48 183.91.67.2 KPB Address-Request = 192.168.2.85
May 10 00:31:48 183.91.67.2 KPB Host-Name = "BPA-AG-PC"
May 10 00:31:48 183.91.67.2 KPB Unknown(81) = 00-00-00-42-50-41-2D-41-47-2D-50-43
May 10 00:31:48 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 10 00:31:48 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific
May 10 00:31:48 KPB dhcp_bsdm sending ack with id 3594588014 to 255.255.255.255
May 10 00:31:48 183.91.67.2 KPB flags = broadcast
May 10 00:31:48 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:31:48 183.91.67.2 KPB yiaddr = 192.168.2.85
May 10 00:31:48 183.91.67.2 KPB siaddr = 192.168.2.1
May 10 00:31:48 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:31:48 183.91.67.2 KPB Msg-Type = ack
May 10 00:31:48 183.91.67.2 KPB Server-Id = 192.168.2.1
May 10 00:31:48 183.91.67.2 KPB Address-Time = 31536000
May 10 00:31:48 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:31:48 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:31:48 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 01:24:12 183.91.67.2 KPB Server-Id = 192.168.1.129
May 10 01:24:12 183.91.67.2 KPB Subnet-Mask = 255.255.255.128
May 10 01:24:12 183.91.67.2 KPB Router = 192.168.1.129
May 10 01:24:12 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 02:11:24 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 02:11:24 183.91.67.2 KPB Router = 192.168.2.1
May 10 02:11:24 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 02:50:02 SRP HotSpot_Gd71: new host detected 00:14:D1:F1:16:8B/192.168.1.19 by UDP :1026 -> 202.169.224.16:123
May 10 02:55:02 SRP HotSpot_Gd71: dynamic host 172.16.1.114 removed: idle timeout
May 10 03:00:31 183.91.67.2 KPB Subnet-Mask = 255.255.255.128
May 10 03:00:31 183.91.67.2 KPB Router = 192.168.1.129
May 10 03:00:31 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 03:21:38 183.91.67.2 KPB Address-Time = 31536000
May 10 03:21:38 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 03:21:38 183.91.67.2 KPB Router = 192.168.2.1
May 10 03:21:38 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 03:49:08 KPB user admin logged in from 110.137.227.147 via winbox
May 10 03:51:12 KPB log rule changed by admin
May 10 03:51:18 KPB log rule changed by admin
May 10 03:51:23 KPB log rule changed by admin
From http://whois.domaintools.com/, I find :
202.152.5.36 = ns.idola.net.id
202.152.0.2 = rajawali.idola.net.id
For last 100 lines :
#tail -100 /var/log/mikrotik.log
For real time :
#tail -f /var/log/mikrotik.log
Tested : event, info, system and warning
I tried to disable log rule or under testing : critical, dhcp, error
Enable log rule : hotspot.
May 9 23:43:46 183.91.67.2 KPB Unknown(81) = 00-00-00-42-50-41-2D-41-47-2D-50-43
May 9 23:43:46 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 9 23:43:46 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific
May 9 23:43:46 KPB dhcp_bsdm sending ack with id 1548336385 to 255.255.255.255
May 9 23:43:46 183.91.67.2 KPB flags = broadcast
May 9 23:43:46 183.91.67.2 KPB ciaddr = 0.0.0.0
May 9 23:43:46 183.91.67.2 KPB yiaddr = 192.168.2.85
May 9 23:43:46 183.91.67.2 KPB siaddr = 192.168.2.1
May 9 23:43:46 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 9 23:43:46 183.91.67.2 KPB Msg-Type = ack
May 9 23:43:46 183.91.67.2 KPB Server-Id = 192.168.2.1
May 9 23:43:46 183.91.67.2 KPB Address-Time = 31536000
May 9 23:43:46 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 9 23:43:46 183.91.67.2 KPB Router = 192.168.2.1
May 9 23:43:46 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 9 23:58:08 KPB dhcp_bu received inform with id 420795606 from 192.168.1.246
May 9 23:58:08 183.91.67.2 KPB Msg-Type = inform
May 9 23:58:08 183.91.67.2 KPB Client-Id = 01-00-50-8D-9F-48-F9
May 9 23:58:08 183.91.67.2 KPB Host-Name = "Windows7-PC"
May 9 23:58:08 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 9 23:58:08 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific,Unknown(252)
May 9 23:58:08 KPB dhcp_bu sending ack with id 420795606 to 255.255.255.255
May 9 23:58:08 183.91.67.2 KPB flags = broadcast
May 9 23:58:08 183.91.67.2 KPB ciaddr = 192.168.1.246
May 9 23:58:08 183.91.67.2 KPB siaddr = 192.168.1.129
May 9 23:58:08 183.91.67.2 KPB chaddr = 00:50:8D:9F:48:F9
May 9 23:58:08 183.91.67.2 KPB Msg-Type = ack
May 9 23:58:08 183.91.67.2 KPB Server-Id = 192.168.1.129
May 9 23:58:08 183.91.67.2 KPB Subnet-Mask = 255.255.255.128
May 9 23:58:08 183.91.67.2 KPB Router = 192.168.1.129
May 9 23:58:08 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:14:15 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:14:15 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:14:15 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:18:50 KPB dhcp_bsdm received request with id 2652037990 from 0.0.0.0
May 10 00:18:50 183.91.67.2 KPB flags = broadcast
May 10 00:18:50 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:18:50 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:18:50 183.91.67.2 KPB Msg-Type = request
May 10 00:18:50 183.91.67.2 KPB Client-Id = 01-00-15-F2-82-D9-39
May 10 00:18:50 183.91.67.2 KPB Address-Request = 192.168.2.85
May 10 00:18:50 183.91.67.2 KPB Host-Name = "BPA-AG-PC"
May 10 00:18:50 183.91.67.2 KPB Unknown(81) = 00-00-00-42-50-41-2D-41-47-2D-50-43
May 10 00:18:50 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 10 00:18:50 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific
May 10 00:18:50 KPB dhcp_bsdm sending ack with id 2652037990 to 255.255.255.255
May 10 00:18:50 183.91.67.2 KPB flags = broadcast
May 10 00:18:50 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:18:50 183.91.67.2 KPB yiaddr = 192.168.2.85
May 10 00:18:50 183.91.67.2 KPB siaddr = 192.168.2.1
May 10 00:18:50 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:18:50 183.91.67.2 KPB Msg-Type = ack
May 10 00:18:50 183.91.67.2 KPB Server-Id = 192.168.2.1
May 10 00:18:50 183.91.67.2 KPB Address-Time = 31536000
May 10 00:18:50 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:18:50 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:18:50 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:31:37 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:31:37 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:31:37 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 00:31:48 KPB dhcp_bsdm received request with id 3594588014 from 0.0.0.0
May 10 00:31:48 183.91.67.2 KPB flags = broadcast
May 10 00:31:48 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:31:48 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:31:48 183.91.67.2 KPB Msg-Type = request
May 10 00:31:48 183.91.67.2 KPB Client-Id = 01-00-15-F2-82-D9-39
May 10 00:31:48 183.91.67.2 KPB Address-Request = 192.168.2.85
May 10 00:31:48 183.91.67.2 KPB Host-Name = "BPA-AG-PC"
May 10 00:31:48 183.91.67.2 KPB Unknown(81) = 00-00-00-42-50-41-2D-41-47-2D-50-43
May 10 00:31:48 183.91.67.2 KPB Class-Id = "MSFT 5.0"
May 10 00:31:48 183.91.67.2 KPB Parameter-List = Subnet-Mask,Domain-Name,Router,Domain-Server,NETBIOS-Name-Server,Unknown(46),Unknown(47),Unknown(31),Static-Route,Classless-Route,Unknown(249),Vendor-Specific
May 10 00:31:48 KPB dhcp_bsdm sending ack with id 3594588014 to 255.255.255.255
May 10 00:31:48 183.91.67.2 KPB flags = broadcast
May 10 00:31:48 183.91.67.2 KPB ciaddr = 0.0.0.0
May 10 00:31:48 183.91.67.2 KPB yiaddr = 192.168.2.85
May 10 00:31:48 183.91.67.2 KPB siaddr = 192.168.2.1
May 10 00:31:48 183.91.67.2 KPB chaddr = 00:15:F2:82:D9:39
May 10 00:31:48 183.91.67.2 KPB Msg-Type = ack
May 10 00:31:48 183.91.67.2 KPB Server-Id = 192.168.2.1
May 10 00:31:48 183.91.67.2 KPB Address-Time = 31536000
May 10 00:31:48 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 00:31:48 183.91.67.2 KPB Router = 192.168.2.1
May 10 00:31:48 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 01:24:12 183.91.67.2 KPB Server-Id = 192.168.1.129
May 10 01:24:12 183.91.67.2 KPB Subnet-Mask = 255.255.255.128
May 10 01:24:12 183.91.67.2 KPB Router = 192.168.1.129
May 10 01:24:12 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 02:11:24 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 02:11:24 183.91.67.2 KPB Router = 192.168.2.1
May 10 02:11:24 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 02:50:02 SRP HotSpot_Gd71: new host detected 00:14:D1:F1:16:8B/192.168.1.19 by UDP :1026 -> 202.169.224.16:123
May 10 02:55:02 SRP HotSpot_Gd71: dynamic host 172.16.1.114 removed: idle timeout
May 10 03:00:31 183.91.67.2 KPB Subnet-Mask = 255.255.255.128
May 10 03:00:31 183.91.67.2 KPB Router = 192.168.1.129
May 10 03:00:31 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 03:21:38 183.91.67.2 KPB Address-Time = 31536000
May 10 03:21:38 183.91.67.2 KPB Subnet-Mask = 255.255.255.0
May 10 03:21:38 183.91.67.2 KPB Router = 192.168.2.1
May 10 03:21:38 183.91.67.2 KPB Domain-Server = 202.152.5.36,202.152.0.2
May 10 03:49:08 KPB user admin logged in from 110.137.227.147 via winbox
May 10 03:51:12 KPB log rule changed by admin
May 10 03:51:18 KPB log rule changed by admin
May 10 03:51:23 KPB log rule changed by admin
From http://whois.domaintools.com/, I find :
202.152.5.36 = ns.idola.net.id
202.152.0.2 = rajawali.idola.net.id
For last 100 lines :
#tail -100 /var/log/mikrotik.log
For real time :
#tail -f /var/log/mikrotik.log
Tested : event, info, system and warning
I tried to disable log rule or under testing : critical, dhcp, error
Enable log rule : hotspot.
07 May 2011
Send Logs MikroTik with Private IP to Linux Server
 Basically, MikroTik with Private IP can send log to Linux Server. With condition, this MikroTik with Private IP, has uplink to another MikroTik with Public IP. Suppose MikroTik RB1100 with Private IP was called SRP and has IP 192.168.1.2. Suppose MikroTik RB1100 with Public IP was called NOC and has IP 183.91.x1.y1. Because IP 183.91.x1.y1 already be set in the file /etc/rsyslog.conf, then on the linux server side does not need to apply the settings again. You just need setting up on the MikroTik SRP.
Basically, MikroTik with Private IP can send log to Linux Server. With condition, this MikroTik with Private IP, has uplink to another MikroTik with Public IP. Suppose MikroTik RB1100 with Private IP was called SRP and has IP 192.168.1.2. Suppose MikroTik RB1100 with Public IP was called NOC and has IP 183.91.x1.y1. Because IP 183.91.x1.y1 already be set in the file /etc/rsyslog.conf, then on the linux server side does not need to apply the settings again. You just need setting up on the MikroTik SRP.On Linux Server, lets /etc/rsyslog.conf file like this
### for mikrotik remote logging
$AllowedSender UDP, 183.91.x1.y1/255.255.255.255
$AllowedSender TCP, 183.91.x1.y1/255.255.255.255
$UDPSenverAddress 183.91.x1.y1
$UDPSenverRun 514
:fromhost-ip, isequal, "183.91.x1.y1" /var/log/mikrotik.log
& ~
On MikroTik SRP
1. Set action from /system logging menu
Name: lognhc
Type: remote
Remote Address: 183.91.x2.y2 (nhc server)
Remote Port: 514
BSD Syslog: enable
Syslog Facility: 3 (daemon)
2. Set Log Rules from /system logging menu
Topics: system
Prefix:
Action: lognhc
Other topics : critical, dhcp, error, event, hotspot, info, system, warning
Already configured: KPB, SRP.
Check the result:

Send Logs MikroTik to Linux Server
 To send remote logging from a MikroTik device to a Linux Server, you must configure on both sides. Its setting itself is very simple but quite confusing for some people. Lets read carefully. I use MikroTik RB1000, RB1100 and RB450G. All kind of these MikroTik like same way to setting.
To send remote logging from a MikroTik device to a Linux Server, you must configure on both sides. Its setting itself is very simple but quite confusing for some people. Lets read carefully. I use MikroTik RB1000, RB1100 and RB450G. All kind of these MikroTik like same way to setting.On Linux Server
[root@nhc ~]# uname -a
Linux nhc.batan.go.id 2.6.25-14.fc9.i686 #1 SMP Thu May 1 06:28:41 EDT 2008 i686 i686 i386 GNU/Linux
[root@nhc ~]# yum install rsyslog
[root@nhc ~]# /etc/rc.d/init.d/rsyslog restart
[root@nhc ~]# mcedit /etc/rsyslog.conf
------------------------------------------------
# Provides UDP syslog reception
# unremark 2 lines below by MSM, 7 May 2011
$ModLoad imudp.so
$UDPServerRun 514
### for mikrotik remote logging
$AllowedSender UDP, 183.91.67.2/255.255.255.255
$AllowedSender TCP, 183.91.67.2/255.255.255.255
$UDPSenverAddress 183.91.67.2
$UDPSenverRun 514
:fromhost-ip, isequal, "183.91.67.2" /var/log/mikrotik.log
& ~
------------------------------------------------
Restart rsyslog daemon :
[root@nhc ~]# /etc/rc.d/init.d/rsyslog restart
On MikroTik
1. Set action from /system logging menu
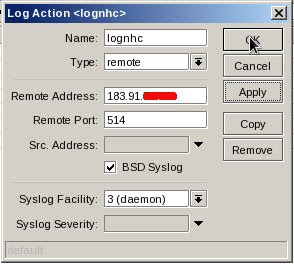 Name: lognhc
Name: lognhcType: remote
Remote Address: 183.91.70.165 (nhc server)
Remote Port: 514
BSD Syslog: enable
Syslog Facility: 3 (daemon)
2. Set Log Rules from /system logging menu
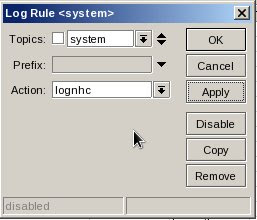 Topics: system
Topics: systemPrefix:
Action: lognhc
Other topics : critical, dhcp, error, event, hotspot, info, system, warning
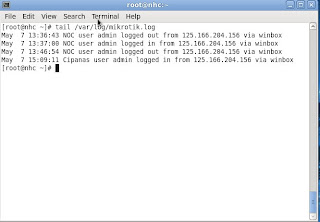
Checking the results:
[root@nhc ~]# tail /var/log/mikrotik.log
May 7 13:36:43 NOC user admin logged out from 125.166.204.156 via winbox
May 7 13:37:00 NOC user admin logged in from 125.166.204.156 via winbox
May 7 13:46:54 NOC user admin logged out from 125.166.204.156 via winbox
To add another mikrotik device
To add more mikrotik devices, just add this command or syntax below to /etc/rsyslog.conf file.
### for cipanas mikrotik remote logging
$AllowedSender UDP, 110.136.158.148/255.255.255.255
$AllowedSender TCP, 110.136.158.148/255.255.255.255
$UDPSenverAddress 110.136.158.148
$UDPSenverRun 514
:fromhost-ip, isequal, "110.136.158.148" /var/log/mikrotik.log
& ~
Don't forget to
1. Restart daemon on Linux Server
[root@nhc ~]# /etc/rc.d/init.d/rsyslog restart
2. Add Action on Mikrotik /system logging (see sample above)
3. Add Log Rules on Mikrotik /system logging (see sample above)
4. Checking the results
[root@nhc ~]# tail /var/log/mikrotik.log
May 7 13:36:43 NOC user admin logged out from 125.166.204.156 via winbox
May 7 13:37:00 NOC user admin logged in from 125.166.204.156 via winbox
May 7 13:46:54 NOC user admin logged out from 125.166.204.156 via winbox
May 7 15:09:11 Cipanas user admin logged in from 125.166.204.156 via winbox
See :
http://handz106.multiply.com/journal/item/83/Mikrotik_remote_logging_and_rsyslog
Next Problem :
How to send logs from MikroTik with Private IP
Send Log From MikroTik with Private IP
MikroTik with Private IP has uplink to MikroTik with Public IP. Suppose MikroTik with Private IP is SRP. And suppose MikroTik with Public IP is NOC. SRP has IP 192.168.1.2. NOC has IP 183.91.67.2. Because IP 183.91.67.2 already be set in the file /etc/rsyslog.conf, then on the linux server side does not need to apply the settings again. You just need setting up on the MikroTik SRP.
On Linux Server, /etc/rsyslog.conf file
### for mikrotik remote logging
$AllowedSender UDP, 183.91.67.2/255.255.255.255
$AllowedSender TCP, 183.91.67.2/255.255.255.255
$UDPSenverAddress 183.91.67.2
$UDPSenverRun 514
:fromhost-ip, isequal, "183.91.67.2" /var/log/mikrotik.log
& ~
On MikroTik SRP
1. Set action from /system logging menu
Name: lognhc
Type: remote
Remote Address: 183.91.70.165 (nhc server)
Remote Port: 514
BSD Syslog: enable
Syslog Facility: 3 (daemon)
2. Set Log Rules from /system logging menu
Topics: system
Prefix:
Action: lognhc
Other topics : critical, dhcp, error, event, hotspot, info, system, warning
How to Change language settings in Windows XP
 This article describes how to change the language in Windows XP. Setting the language does not change the language of Windows menus and dialogs, but it does allow you to display text in other languages and to enter text in other languages. Some languages (typically Asian languages) will not appear correctly in the eWebEditPro menus and dialogs unless the default language matches the language of the eWebEditPro locale XML data. Multiple languages will appear in the editor's content Window regardless of the language chosen for the menus and dialogs.
This article describes how to change the language in Windows XP. Setting the language does not change the language of Windows menus and dialogs, but it does allow you to display text in other languages and to enter text in other languages. Some languages (typically Asian languages) will not appear correctly in the eWebEditPro menus and dialogs unless the default language matches the language of the eWebEditPro locale XML data. Multiple languages will appear in the editor's content Window regardless of the language chosen for the menus and dialogs.Changing the language does not change the language of the menus and dialogs of Windows or Windows applications like Internet Explorer. For more information on changing the language of Windows itself and IE, see the references below.
Language settings in Windows 95/98/Me are significantly different and beyond the scope of this article. Windows NT does not support fully changing the language from English to Asian. The native version of Windows NT is required to use Japanese, Chinese, or Korean.
Set a default language of the system to match the language you wish to display. You may need to install the language from the Windows Setup CD-ROM. You may need to restart Windows after selecting a new system language.
Steps to change the default system language (Windows XP)
- Open the Control Panel.
- Open Regional and Language Options.
- Click the Languages tab.
- Ensure Supplemental language support items are checked.
- Click the Advanced tab.
- Select the language from the list in the Language for non-Unicode programs.
Send Logs MikroTik to Email
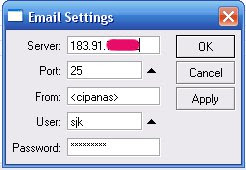 MikroTik logs are not stored permanently in the memory MikroTik, because storage space reasons. While there are some very important logs for our. For this reason, we need to send logs to another system, such as email. To send logs to an email, you can use /tool email menu and /system logging menu.
MikroTik logs are not stored permanently in the memory MikroTik, because storage space reasons. While there are some very important logs for our. For this reason, we need to send logs to another system, such as email. To send logs to an email, you can use /tool email menu and /system logging menu.1. Set email account from /tool email menu
Server: 183.91.x.y (mail server address)
Port: 25
From: <cipanas>
User: sjk
Password:******
In this case, I want send email to sjk@mydomain.com, and I want the email sender is cipanas, where the router was placed.
2. Set action from /system logging menu
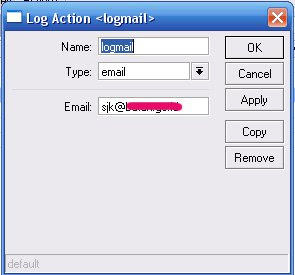
Name: logmail
Type: email
Email: sjk@mydomain.com
You can change "logmail" with your own word. And please change sjk@mydomain.com with your email address.
3. Set Log Rules from /system logging menu
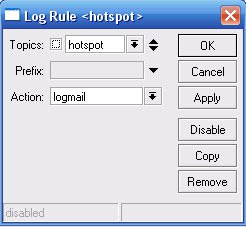
Topics: system
Prefix:
Action: logmail
Topics: hotspot
Prefix:
Action: logmail
Other topics : critical, dhcp, error, event, hotspot, info, system, warning, !debug.
Next effort : send logs to linux server, than show up on web server.
PSJ and BDG not set.
See :
http://handz106.multiply.com/journal/item/83/Mikrotik_remote_logging_and_rsyslog
06 May 2011
Problem with Maximum Resolution DELL U2711 Flat Panel Monitor
Setting the Maximum Resolution
If you have a Dell desktop or portable computer:
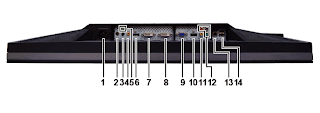
DELL U2711 have many input, that are :
I used VGA Card NVIDIA GeForce FX 5500 256MB with 2 input, VGA Input and DVI-D Input.
- Right-click on the desktop and select Properties.
- Select the Settings tab.
- Set the screen resolution to 2560 x 1440 (DVI and DisplayPort) or 2048 x 1152 (VGA) or 1080p (HDMI, Component).
- Click OK.
If you have a Dell desktop or portable computer:
- Go to support.dell.com, enter your service tag, and download the latest driver for your graphics card.
If you are using a non-Dell computer (portable or desktop):
- Go to the support site for your computer and download the latest graphic drivers.
- Go to your graphics card website and download the latest graphic drivers.
DELL U2711 have many input, that are :
- VGA input
- DVI-D 1 input
- DVI-D 2 input
- DisplayPort input
- HDMI input
- Component video input
- Composite video input

Bottom view
| Label | Description |
| 1 | AC power cord connector |
| 2 | DC power connector for Dell™ Soundbar |
| 3 | Audio out (rear) |
| 4 | Audio out (SUB/CTR) |
| 5 | Audio out (front) |
| 6 | DisplayPort connector |
| 7 | DVI connector-1 |
| 8 | DVI connector-2 |
| 9 | VGA connector |
| 10 | HDMI connector |
| 11 | Composite video connector |
| 12 | Component video connectors |
| 13 | USB upstream port |
| 14 | USB downstream ports |
I used VGA Card NVIDIA GeForce FX 5500 256MB with 2 input, VGA Input and DVI-D Input.
03 May 2011
Cain & Abel v4.9.35, Testing Results
 To test the security systems on multiple servers, I used Cain & Abel version 4.9.35 for Windows XP. Before I do the testing, I have to configure the program to select a specific adapter. For instance, I choose a NIC rather than a Wireless Adapter. Use the Configure menu -> click the Sniffer tab -> click \Device\NPF_bla bla bla -> OK. Choose the Sniffer tab, and than Start Sniffer icon. Check out HTTP group.
To test the security systems on multiple servers, I used Cain & Abel version 4.9.35 for Windows XP. Before I do the testing, I have to configure the program to select a specific adapter. For instance, I choose a NIC rather than a Wireless Adapter. Use the Configure menu -> click the Sniffer tab -> click \Device\NPF_bla bla bla -> OK. Choose the Sniffer tab, and than Start Sniffer icon. Check out HTTP group.The results :
Secure : Yahoo Mail, ssh to nhc, Pustaka Iptek, Blogger, Winbox
Unsecure : Webmail, ftp to nhc, SITP, SIPL,
No checked : wcm, raker, help desk sjk, hotspot
01 May 2011
Wireless LAN Security Summary
Wireless LAN Security Summary based on ISO 27001/ISO17799 are :
1. Develop an agency security policy that addresses the use of wireless technology, including 802.11.
A security policy is the foundation on which other countermeasures—the operational and technical ones—are rationalized and implemented. A documented security policy allows an organization to define acceptable architecture, implementation, and uses for 802.11 wireless technologies.
2. Ensure that users on the network are fully trained in computer security awareness and the risks associated with wireless technology (e.g., 802.11).
A security awareness program helps users to establish good security practices to prevent inadvertent or malicious intrusions into an organization’s information systems.
3. Perform a risk assessment to understand the value of the assets in the agency that need protection.
Understanding the value of organizational assets and the level of protection required is likely to enable more cost-effective wireless solutions that provide an appropriate level of security.
4. Ensure that the client NIC and AP support firmware upgrades so that security patches may be deployed as they become available (prior to purchase).
Wireless products should support upgrade and patching of firmware to be able to take advantage of wireless security enhancements and fixes.
5. Perform comprehensive security assessments at regular and random intervals (including validating that rogue APs do not exist in the 802.11 WLAN) to fully understand the wireless network security posture.
Security assessments, or audits, are an essential tool for checking the security posture of a WLAN and for determining corrective action to make sure it stays secure. Random checks ensure that the security posture is maintained beyond periods of assessment.
6. Ensure that external boundary protection is in place around the perimeter of the building or buildings of the agency.
The external boundaries should be secured to prevent malicious physical access to an organization’s information system infrastructure such as a fence or locked doors.
7. Deploy physical access controls to the building and other secure areas (e.g., using photo IDs or card badge readers).
Identification badges or physical access cards help to ensure that only authorized personnel have access to gain entry to a facility.
8. Complete a site survey to measure and establish the AP coverage for the agency.
Proper placement of Access Points will help ensure that there is adequate wireless coverage of the environment while minimizing exposure to external attack. The site survey should result in a report that proposes AP locations, determines coverage areas, and assigns radio channels to each AP and that ensures that the coverage range does not expose APs to potential malicious activities.
9. Take a complete inventory of all APs and 802.11 wireless devices.
A complete inventory list of APs and 802.11 wireless devices can be referenced when conducting an audit for unauthorized use of wireless technologies.
10. Ensure that wireless networks are not used until they comply with the agency’s security policy.
Security policy enforcement is vital for ensuring that only authorized APs and 802.11 wireless devices are operating in compliance with the organization’s wireless security policy.
Source : http://www.controlscada.com/download-free-iso-27001iso17799-wireless-lan-security-summary
1. Develop an agency security policy that addresses the use of wireless technology, including 802.11.
A security policy is the foundation on which other countermeasures—the operational and technical ones—are rationalized and implemented. A documented security policy allows an organization to define acceptable architecture, implementation, and uses for 802.11 wireless technologies.
2. Ensure that users on the network are fully trained in computer security awareness and the risks associated with wireless technology (e.g., 802.11).
A security awareness program helps users to establish good security practices to prevent inadvertent or malicious intrusions into an organization’s information systems.
3. Perform a risk assessment to understand the value of the assets in the agency that need protection.
Understanding the value of organizational assets and the level of protection required is likely to enable more cost-effective wireless solutions that provide an appropriate level of security.
4. Ensure that the client NIC and AP support firmware upgrades so that security patches may be deployed as they become available (prior to purchase).
Wireless products should support upgrade and patching of firmware to be able to take advantage of wireless security enhancements and fixes.
5. Perform comprehensive security assessments at regular and random intervals (including validating that rogue APs do not exist in the 802.11 WLAN) to fully understand the wireless network security posture.
Security assessments, or audits, are an essential tool for checking the security posture of a WLAN and for determining corrective action to make sure it stays secure. Random checks ensure that the security posture is maintained beyond periods of assessment.
6. Ensure that external boundary protection is in place around the perimeter of the building or buildings of the agency.
The external boundaries should be secured to prevent malicious physical access to an organization’s information system infrastructure such as a fence or locked doors.
7. Deploy physical access controls to the building and other secure areas (e.g., using photo IDs or card badge readers).
Identification badges or physical access cards help to ensure that only authorized personnel have access to gain entry to a facility.
8. Complete a site survey to measure and establish the AP coverage for the agency.
Proper placement of Access Points will help ensure that there is adequate wireless coverage of the environment while minimizing exposure to external attack. The site survey should result in a report that proposes AP locations, determines coverage areas, and assigns radio channels to each AP and that ensures that the coverage range does not expose APs to potential malicious activities.
9. Take a complete inventory of all APs and 802.11 wireless devices.
A complete inventory list of APs and 802.11 wireless devices can be referenced when conducting an audit for unauthorized use of wireless technologies.
10. Ensure that wireless networks are not used until they comply with the agency’s security policy.
Security policy enforcement is vital for ensuring that only authorized APs and 802.11 wireless devices are operating in compliance with the organization’s wireless security policy.
Source : http://www.controlscada.com/download-free-iso-27001iso17799-wireless-lan-security-summary
Comparison between COBIT, ITIL and ISO 27001
Many friend of mine keep asking me about what is should be implemented first to improve their information system management: whether taking Cobit, ITIL, or ISO27001. And the next question usually which one is the easiest to be implemented in their company.
To be able to answer this question, let me tell you the definition of this three major standard in information system, who has a little bit difference in basic concept.
COBIT
Cobit is stand for Control Objective over Information and Related Technology. Cobit issued by ISACA (Information System Control Standard) a non profit organization for IT Governance. The Cobit main function is to help the company, mapping their IT process to ISACA best practices standard. Cobit usually choosen by the company who performing information system audit, whether related to financial audit or general IT audit.
ITIL
ITIL is stand for Information Technology Library. ITIL issued by OGC, is a set of framework for managing IT Service Level. Although ITIL is quite similar with COBIT in many ways, but the basic difference is Cobit set the standard by seeing the process based and risk, and in the other hand ITIL set the standard from basic IT service.
ISO27001
ISO27001 is much more different between COBIT and ITIL, because ISO27001 is a security standard, so it has smaller but deeper domain compare to COBIT and ITIL.
Here is the detail table of comparison between this three standard
What should be implemented first?
There's no exact answer about this question, but i think its really depend on your company and your requirement. Most of company start to implemented Cobit first because its cover general information system. And after that they usually choose between ITIL or ISO27001.
Another consideration is about budget and authoritive. Cobit implementation usually run from internal audit budget and ITIL or ISO27001 usually performed using IT departement budget. This consideration usually makes what kind of standard to implemented first become depend on management policy.
What is the easiest standard?
From the implementatation view, ITIL is the easiest standard to be implemented. Because, ITIL could be implemented partially and still not have impact on performance. Example, if IT departement lack of budget and he could choose to implement IT Service Delivery layer only, and the next year he will try to implement IT Release Management or IT Problem Management.<
However COBIT and ISO27001 is quite difficult to be implemented partially, since it should see a process in bigger view first before they could implemented partially.
How to choose the right vendor?
Many vendor said that he could help your company to implement these standard effectively, in fact there is no one solution for all. Usually the COBIT vendor come from Publci Accounting Firm who has an IT Audit arm, eg PWC, DTT, KPMG, EY. This type of vendor is best choice for COBIT since they also work for COBIT implementation derivative such as COBIT for Sarbanes Oxley.
The other standard ITIL and ISO27001 usually come from General IT Consulting Company, eg. IBM, Accenture. And for ISO27001 most of IT networking company also could offer this standard consultation.
Do you have any other opinion with this comparison?
Others referrence:
ISACA: Aligning COBIT, ITIL and ISO 17799 for Business Benefit
Download Hundreds of Complimentary Industry Resources
Get hundreds of popular Industry magazines, white papers, webinars, podcasts, and more; all available at no cost to you. With more than 600 complimentary offers, you'll find plenty of titles to suit your professional interests and needs. Click Here and Sign up today!
Source : http://www.securityprocedure.com/
To be able to answer this question, let me tell you the definition of this three major standard in information system, who has a little bit difference in basic concept.
COBIT
Cobit is stand for Control Objective over Information and Related Technology. Cobit issued by ISACA (Information System Control Standard) a non profit organization for IT Governance. The Cobit main function is to help the company, mapping their IT process to ISACA best practices standard. Cobit usually choosen by the company who performing information system audit, whether related to financial audit or general IT audit.
ITIL
ITIL is stand for Information Technology Library. ITIL issued by OGC, is a set of framework for managing IT Service Level. Although ITIL is quite similar with COBIT in many ways, but the basic difference is Cobit set the standard by seeing the process based and risk, and in the other hand ITIL set the standard from basic IT service.
ISO27001
ISO27001 is much more different between COBIT and ITIL, because ISO27001 is a security standard, so it has smaller but deeper domain compare to COBIT and ITIL.
Here is the detail table of comparison between this three standard
| AREA | COBIT | ITIL | ISO27001 |
| Function | Mapping IT Process | Mapping IT Service Level Management | Information Security Framework |
| Area | 4 Process and 34 Domain | 9 Process | 10 Domain |
| Issuer | ISACA | OGC | ISO Board |
| Implementation | Information System Audit | Manage Service Level | Compliance to security standard |
| Consultant | Accounting Firm, IT Consulting Firm | IT Consulting firm | IT Consulting firm, Security Firm, Network Consultant |
What should be implemented first?
There's no exact answer about this question, but i think its really depend on your company and your requirement. Most of company start to implemented Cobit first because its cover general information system. And after that they usually choose between ITIL or ISO27001.
Another consideration is about budget and authoritive. Cobit implementation usually run from internal audit budget and ITIL or ISO27001 usually performed using IT departement budget. This consideration usually makes what kind of standard to implemented first become depend on management policy.
What is the easiest standard?
From the implementatation view, ITIL is the easiest standard to be implemented. Because, ITIL could be implemented partially and still not have impact on performance. Example, if IT departement lack of budget and he could choose to implement IT Service Delivery layer only, and the next year he will try to implement IT Release Management or IT Problem Management.<
However COBIT and ISO27001 is quite difficult to be implemented partially, since it should see a process in bigger view first before they could implemented partially.
How to choose the right vendor?
Many vendor said that he could help your company to implement these standard effectively, in fact there is no one solution for all. Usually the COBIT vendor come from Publci Accounting Firm who has an IT Audit arm, eg PWC, DTT, KPMG, EY. This type of vendor is best choice for COBIT since they also work for COBIT implementation derivative such as COBIT for Sarbanes Oxley.
The other standard ITIL and ISO27001 usually come from General IT Consulting Company, eg. IBM, Accenture. And for ISO27001 most of IT networking company also could offer this standard consultation.
Do you have any other opinion with this comparison?
Others referrence:
ISACA: Aligning COBIT, ITIL and ISO 17799 for Business Benefit
Download Hundreds of Complimentary Industry Resources
Get hundreds of popular Industry magazines, white papers, webinars, podcasts, and more; all available at no cost to you. With more than 600 complimentary offers, you'll find plenty of titles to suit your professional interests and needs. Click Here and Sign up today!
Source : http://www.securityprocedure.com/
WikiLeaks Cable about Chinese Hacking of U.S. Networks
 We know it's prevalent, but there's some new information:
We know it's prevalent, but there's some new information:Secret U.S. State Department cables, obtained by WikiLeaks and made available to Reuters by a third party, trace systems breaches -- colorfully code-named "Byzantine Hades" by U.S. investigators -- to the Chinese military. An April 2009 cable even pinpoints the attacks to a specific unit of China's People's Liberation Army.
Privately, U.S. officials have long suspected that the Chinese government and in particular the military was behind the cyber-attacks. What was never disclosed publicly, until now, was evidence.
U.S. efforts to halt Byzantine Hades hacks are ongoing, according to four sources familiar with investigations. In the April 2009 cable, officials in the State Department's Cyber Threat Analysis Division noted that several Chinese-registered Web sites were "involved in Byzantine Hades intrusion activity in 2006."
The sites were registered in the city of Chengdu, the capital of Sichuan Province in central China, according to the cable. A person named Chen Xingpeng set up the sites using the "precise" postal code in Chengdu used by the People's Liberation Army Chengdu Province First Technical Reconnaissance Bureau (TRB), an electronic espionage unit of the Chinese military. "Much of the intrusion activity traced to Chengdu is similar in tactics, techniques and procedures to (Byzantine Hades) activity attributed to other" electronic spying units of the People's Liberation Army, the cable says.
[...]
What is known is the extent to which Chinese hackers use "spear-phishing" as their preferred tactic to get inside otherwise forbidden networks. Compromised email accounts are the easiest way to launch spear-phish because the hackers can send the messages to entire contact lists.
The tactic is so prevalent, and so successful, that "we have given up on the idea we can keep our networks pristine," says Stewart Baker, a former senior cyber-security official at the U.S. Department of Homeland Security and National Security Agency. It's safer, government and private experts say, to assume the worst -- that any network is vulnerable.
Two former national security officials involved in cyber-investigations told Reuters that Chinese intelligence and military units, and affiliated private hacker groups, actively engage in "target development" for spear-phish attacks by combing the Internet for details about U.S. government and commercial employees' job descriptions, networks of associates, and even the way they sign their emails -- such as U.S. military personnel's use of "V/R," which stands for "Very Respectfully" or "Virtual Regards."
The spear-phish are "the dominant attack vector. They work. They're getting better. It's just hard to stop," says Gregory J. Rattray, a partner at cyber-security consulting firm Delta Risk and a former director for cyber-security on the National Security Council.
Spear-phish are used in most Byzantine Hades intrusions, according to a review of State Department cables by Reuters. But Byzantine Hades is itself categorized into at least three specific parts known as "Byzantine Anchor," "Byzantine Candor," and "Byzantine Foothold." A source close to the matter says the sub-codenames refer to intrusions which use common tactics and malicious code to extract data.
A State Department cable made public by WikiLeaks last December highlights the severity of the spear-phish problem. "Since 2002, (U.S. government) organizations have been targeted with social-engineering online attacks" which succeeded in "gaining access to hundreds of (U.S. government) and cleared defense contractor systems," the cable said. The emails were aimed at the U.S. Army, the Departments of Defense, State and Energy, other government entities and commercial companies.
By the way, reading this blog entry might be illegal under the U.S. Espionage Act:
Dear Americans: If you are not "authorized" personnel, but you have read, written about, commented upon, tweeted, spread links by "liking" on Facebook, shared by email, or otherwise discussed "classified" information disclosed from WikiLeaks, you could be implicated for crimes under the U.S. Espionage Act -- or so warns a legal expert who said the U.S. Espionage Act could make "felons of us all."
As the U.S. Justice Department works on a legal case against WikiLeak's Julian Assange for his role in helping publish 250,000 classified U.S. diplomatic cables, authorities are leaning toward charging Assange with spying under the Espionage Act of 1917. Legal experts warn that if there is an indictment under the Espionage Act, then any citizen who has discussed or accessed "classified" information can be arrested on "national security" grounds.
Maybe I should have warned you at the top of this post.
Source : http://www.schneier.com/
30 April 2011
Computer Security at Nuclear Facilities
 The aspects that must be considered when applying computer security are wired network, wireless network, computer servers (include use secure OS), application software (mail, web, database), network devices (gateway, router, firewall, switch), computer room, network (wired and wireless) monitoring tools, testing/detecting/monitoring software tools, anti virus, IDS/IPS, cryptography, early warning system. The most important is the awareness of users. Without this, every effort be useless.
The aspects that must be considered when applying computer security are wired network, wireless network, computer servers (include use secure OS), application software (mail, web, database), network devices (gateway, router, firewall, switch), computer room, network (wired and wireless) monitoring tools, testing/detecting/monitoring software tools, anti virus, IDS/IPS, cryptography, early warning system. The most important is the awareness of users. Without this, every effort be useless.Computer Security is talking about how to prevent and detect from unauthorized access from unwanted users from certain computer system. Prevent to protect.
Rule 10/90, that is 10% technique, 90% habit.
Example :
- Yes, you need a password
- How to save it
- How to written down
- Don't using easy password
- Don't using the same password
- Don't give somebody else
- Change password periodically
- Remember to logout
- Make sure already logout
- Always login on secure system, no key logger, no cam, no spyware
Bugs and Security holes
- Bugs : error in computer system.
- Vulnerabilities (security hole) : bugs that enable user to violate security policy. For instance: wired network, wireless network and Operating Systems.
- Security hole : errors in design, errors in implementation, errors in maintenance. For instance: hand made applications, hand made programs, CMS.
Catagories computer misuse :
- External
- Hardware misuse
- Masquerading
- Pest Program
- By passes
- Active misuse
- Passive misuse
- Inactive misuse
- Indirect misuse
- Administration access : allows administrative activies on the computer, above and beyond that of a normal user
- Read restricted access : allows access to files that can normally not be accessed, or can view information not supposed to be viewed that may lead to a security compromise
- Reguler user access : access as a regular user has a strong degree of severity because these are typically many more ways interact with the system than without access at all
- Spoofing : allows the intruder to assume the identity of a user, computer, or network entity. This can result in other systems trusting the intruder and allow a system compromise
- Non-detectability : arises when a logging system has been disabled or otherwise malfunction. This can allow an intruder to perform actions that cannot be recorded.
- Deniel of Service : lowest degree of severity
- Nikto, looking for detail and possibility of vulnerbility.
- w3bfuktor, directories
- sqler.sh, sql injection
- hping, testing for detail packet handling, blocking by firewall or not
- nmap, open port
Cheak out :
Top 100 Network Security Tools, include Nessus, WireShark, Hping, Cain and Abel, Nikto, GFI LANguard
Top 10 Web Vulnerability Scanners, include Nikto
Top 10 Vulnerability Scanners, include Nessus, GFI LANguard
Top 11 Packet Sniffers, include WireShark, Cain and Abel, NetStumbler,
Top 5 Wireless Tools, include NetStumbler
Top 4 Packet Crafting Tools, include hping
Top 6 Traffic Monitoring Tools, include Ntop, EtherApe
Top 5 Security-Oriented Operating Systems, include BackTrack, Knoppix
Top 4 Port Scanners, include Superscan, Angry IP Scanner
John the Ripper for Windows Download
Cracking password dengan John The Ripper
Jika tidak ada file /etc/shadow, bisa juga pakai file /etc/master.passwd
How to Shutdown Open VMS
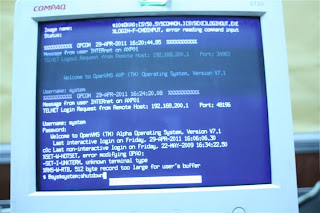 DEC AlphaServer 2100 were based on the DEC Alpha 64-bit microprocessor, has call name "Sable Family". Supported operating system for this server are Tru64 UNIX, Windows NT and OpenVMS. The server operated since 1996 to replaced DEC VAX 8550. To shutdown OpenVMS on this Digital 2100 is very simple. You just login as system and run command line "@sys$system:shutdown". Than answer a few questions with just push Enter button.
DEC AlphaServer 2100 were based on the DEC Alpha 64-bit microprocessor, has call name "Sable Family". Supported operating system for this server are Tru64 UNIX, Windows NT and OpenVMS. The server operated since 1996 to replaced DEC VAX 8550. To shutdown OpenVMS on this Digital 2100 is very simple. You just login as system and run command line "@sys$system:shutdown". Than answer a few questions with just push Enter button.$ @sys$system:shutdown
Answer these questions :
How many minutes until final shutdwon [0]:
Reason for shutdown [Standalone]:
Do you want to
spin down the disk volume [NO]?
Do you want to invoke the site-specific shutdown procedure [YES]?
Should an automatic system reboot be performed [NO]?
When will the system be rebooted [later]:
Shutdown options (enter as a comma-separated list):
 After you answer these questions with press the Enter button as a default, server will reboot. You will see the prompt "P00>>>". Now , you can switch of power button.
After you answer these questions with press the Enter button as a default, server will reboot. You will see the prompt "P00>>>". Now , you can switch of power button.See : http://en.wikipedia.org/wiki/AlphaServer
24 April 2011
Europe Travelling Notes
Vienna Hostel Hütteldorf
Address : Schlossberggasse 8, Vienna, Austria A-1130.
Modern Hostel near the famous Schönbrunn Palace and 15 minutes from the centre by underground. FREE breakfast, free bedlinen, free Internet, free WiFi. Dorms with 2, 4, 6 and 7 beds, in total 296 beds! Why look further?! Stay with us!
Shared : €14.50, Private : €15.50. When I chek for May 14 - May 21, 2011, the price is €18 per person.
Modern hostel with 50-year-old tradition!
Welcome to the first hostel in Austria!
Location:
Here you can find the perfect combination of city and green environment, culture and nature, fun and relaxation:
The Youth Hostel Hütteldorf is right on the subway line U4, which brings you in 20 minutes to downtown and in 10 minutes to the Schönbrunn Palace and the Naschmarkt (Vienna’s most popular market). The house itself is situated on the edge of the forest, surrounded by numerous walking and bike trails and a large garden. The unique features and the sensational price make us irresistible to every hostel traveller.
See more : http://www.hostelbookers.com/hostels/austria/vienna/
Cheap Flights from Vienna to Moscow - VIE to MOW
Vienna, AT to Moscow, RU
Depart: Sunday, 5/22/2011 | Return: Tuesday, 5/24/2011
Price US$334 (Roundtrip price), Taxes & fees incl.
Airline : Aeroflot
Depart : VIE at 12:30 AM, Arrive : SVO at 5:05 AM Nonstop, Duration : 2h 35m
Depart : SVO at 4:10 PM, Arrive : VIE 4:50 PM Nonstop, Duration : 2h 40m
Price US$268 (One-way price), Taxes & fees incl.
Airline : Aeroflot
Depart : VIE at 12:30 AM, Arrive : SVO 5:05 AM Nonstop, Duration : 2h 35m
SVO = Shemeretyevo Airport, Moscow
See more : http://www.farecompare.com/flights/Vienna-VIE/Moscow-MOW/market.html
Moscow Hostel ?
Trains between Russia and Germany
There are quite a few ways to travel from Europe to Russia including trains from Germany, Finland, Poland and all of the Baltic States. Please note: a transit visa is required for trains that stop or go through Belarus. If you travel from Germany there are 2 direct trains to Russia one going from Berlin to Moscow and the other from Berlin to St. Petersburg. Also there are a few daily trains from Berlin to Warsaw. To receive Russian train schedules and Russian train ticket prices as well as to have the opportunity to order Russian train tickets online, please use our Russian train tickets page or use the search engine on this page.
Train Berlin №13 Moscow - Berlin (Germany)
Departure Moscow-Belorusskaia : 08:00
Arrival Berlin Zoo (Germany) : 08:52 (next day)
Total hours : 1d 04:52
Price per person for May 23, 2011 : US$ 375 (2nd Class), no 3rd Class.
The route : Moscow Belorusskaia - Viazma - Smolensk - Orsha Center - Minsk Pas - Brest C - Terespol - Lukow - Warszawa Centralna - Warszawa Centralna - Poznan Glowny - Rzepin - Frankfurt Oder - Berlin Ost (East Berlin) - Berlin Gl. - Berlin Zoo.
Train Berlin №14 Berlin (Germany) - Moscow
Departure Berlin (Germany) : 15:24
Arrival Moscow : 20:35
Total hours : 1d 01:11
See more : http://www.expresstorussia.com/moscow-berlin-train.html
Berlin Hostel ?
Trains between Berlin and Amsterdam
Berlin Amsterdam Outbound 25/05/2011 Morning
Outbound : 04:04 at BERLIN HBF
Arrival : 11:08 at AMSTERDAM SCHIPHOL
Duration : 7h 04m (1 connection or transfer)
ICE 646 - Reservation not included
Train 242 - Reservation not included
Flexible Second Class : €114.20
Outbound : 08:04 at BERLIN HBF
Arrival : 15:08 at AMSTERDAM SCHIPHOL
Duration : 7h 04m (Direct)
Train 148 - Reservation not included
Flexible Second Class : €114.20
Outbound : 11:34 at BERLIN HBF
Arrival : 20:25 at AMSTERDAM CS
Duration : 8h 51m (1 connection or transfer)
ICE 599 - Reservation included
ICE 122 - Reservation included
Flexible Second Class : €245.20
Outbound : 14:03 at BERLIN HBF
Arrival : 21:08 at AMSTERDAM SCHIPHOL
Duration : 7h 05m (Direct)
Train 142 - Reservation not included
Flexible Second Class : €114.20
Outbound : 17:45 at BERLIN HBF
Arrival : 09:03 at AMSTERDAM CS
Duration : 15h 18m (1 connection or transfer)
ICE 1093 - Reservation included
Train 418 - Reservation included
Best second class : €188.00
Flexible Second Class : €278.00
See more : http://www.raileurope-world.com/
By bus from Berlin to Amsterdam
Departure : 25-05-2011 (21:30)
Arrival : 26-05-2011 (07:15)
From : Berlin, ZOB Am Funkturm
To : Amsterdam, Amstel Station/Eurolines
Promo (one way) : -
Price (one way) : €58.00
Departure : 26-05-2011 (19:30)
Arrival : 27-05-2011 (05:45)
From : Berlin, ZOB Am Funkturm
To : Amsterdam, Amstel Station/Eurolines
Promo (one way) : €33.00
Price (one way) : €58.00
Departure : 26-05-2011 (21:30)
Arrival : 27-05-2011 (07:15)
From : Berlin, ZOB Am Funkturm
To : Amsterdam, Amstel Station/Eurolines
Promo (one way) : -
Price (one way) : €58.00
Departure : 27-05-2011 (19:30)
Arrival : 28-05-2011 (05:45)
From : Berlin, ZOB Am Funkturm
To : Amsterdam, Amstel Station/Eurolines
Promo (one way) : €40.60
Price (one way) : €58.00
Departure : 27-05-2011 (21:30)
Arrival : 28-05-2011 (07:15)
From : Berlin, ZOB Am Funkturm
To : Amsterdam, Amstel Station/Eurolines
Promo (one way) : -
Price (one way) : €58.00
See more : http://www.touring.de/index.php?id=1089&L=1 or http://www.eurolines.com/
Amsterdam Hostel?
Amsterdam to London by Bus
Departure (Amsterdam) : Sunday, May 29, 2011 8:30 AM
Arrival (London) : Sunday, May 29, 2011 6:15 PM
Departure (Amsterdam) : Sunday, May 29, 2011 10:00 AM
Arrival (London) : Sunday, May 29, 2011 8:10 PM
Departure (Amsterdam) : Sunday, May 29, 2011 7:30 PM
Arrival (London) : Monday, May 30, 2011 6:30 AM
Departure (Amsterdam) : Sunday, May 29, 2011 10:30 PM
Arrival (London) : Monday, May 30, 2011 8:45 AM
Departure (Amsterdam) : Monday, May 30, 2011 8:30 AM
Arrival (London) : Monday, May 30, 2011 6:15 PM
Departure (Amsterdam) : Monday, May 30, 2011 10:00 AM
Arrival (London) : Monday, May 30, 2011 8:10 PM
Departure (Amsterdam) : Monday, May 30, 2011 7:30 PM
Arrival (London) : Tuesday, May 31, 2011 6:30 AM
Departure (Amsterdam) : Monday, May 30, 2011 10:30 PM
Arrival (London) : Tuesday, May 31, 2011 8:45 AM
Departure : Amstelstn.Eurolines Kantoor, Amsterdam
Arrival : Victoria Coach Station, London
Transfer countries : Nederland,Belgie,Frankrijk,Engeland
Cost of your selection One way for 1 Adult (P) : €22.00
S : Standard ticket
P : (Super) Promo ticket
Promo and Super Promo tickets are our best value range of fares available (Promo and Super Promo conditions). If you prefer maximum flexibility to change or cancel your booking we recommend you select a standard ticket.
See more : http://www.eurolines.nl/eng/?lang=ENG
London - Derby (Edensor Village, County Derbyshire) by Bus
Leaving
LONDON (Victoria Coach Station) to Derby — 29 May 2011
*Fares from: Fares based on your passenger selections. The fares listed below are offered only as part of a return journey. Our lowest fares sell out quickly: To avoid disappointment, please choose a fare as soon as possible.
Departs From To Arrives Duration Changes Fares from*
19:30 LONDON (Victoria Coach Station) Derby 22:35 3h 5m 0 £10.50
20:30 LONDON (Victoria Coach Station) Derby 23:50 3h 20m 0 £13.60
23:30 LONDON (Victoria Coach Station) Derby 02:45 3h 15m 0 £5.50
Returning
Derby to LONDON (Victoria Coach Station) — 30 May 2011
*Fares from Fares based on your passenger selections. The fares listed below are offered only as part of a return journey, and may change based on your journey selection. Our lowest fares sell out quickly: To avoid disappointment, please choose a fare as soon as possible.
Departs From To Arrives Duration Changes Fares from*
16:40 Derby LONDON (Victoria Coach Station) 21:30 4h 50m 1 £12.50
17:55 Derby LONDON (Victoria Coach Station) 21:40 3h 45m 0 £5.50
18:45 Derby LONDON (Victoria Coach Station) 23:45 5h 00m 1 £12.50
19:45 Derby LONDON (Victoria Coach Station) 00:10 4h 25m 1 £12.50
See more : http://www.eurolines.co.uk/coach/index.aspx
London - Paris by TGV
See : http://www.raileurope-world.com/
Paris - Vienna by Bus Eurolines
Paris Gallieni Porte Bagnolet to Wien-Erdbergstrasse by Eurolines
departure : Friday 03 June 2011 14:15
arrival : Saturday 04 June 2011 07:15
Price = €50.00
Bus station at Paris : Paris Gallieni Porte Bagnolet, Paris Place de Clichy, Paris Porte de Charenton, Paris Roissy Charles de Gaulle.
See : http://www.eurolines.fr/ENG/?lang=ENG
Misc
Rate :
EUR 1 = IDR 12829.30 (sale) , IDR 12437.30 (buy)
Fri, May 13, 2011 : CKG
Sat, May 14, 2011 : VIENNA
Mon, May 16, 2011 : TM
...
Fri, May 20, 2011 : TM
Sat, May 21, 2011 (00:30 AM) : VIENNA US$268 by Aeroflot
Sat, May 21, 2011 (05:05 AM) : MOSCOW (Shemeretyevo = SVO)
Mon, May 23, 2011 (08:00 AM) : MOSCOW US$ 375 by Train Berlin №13 Moscow - Berlin
Tue, May 24, 2011 (08:52 AM) : BERLIN
Thu, May 26, 2011 (19:30) : Berlin, ZOB Am Funkturm €58.00 by Bus
Fri, May 27, 2011 (05:45) : Amsterdam, Amstel Station/Eurolines
Sun, May 29, 2011 (08:30 AM) : Amsterdam (Amstelstn.Eurolines Kantoor) €22.00 by Bus
Sun, May 29, 2011 (06:15 PM) : London (Victoria Coach Station)
Sun, May 29, 2011 (19:30) : London by Bus £10.50
Sun, May 29, 2011 (22:35) : Derby
Mon, May 30, 2011 (18:45) : Derby by Bus £12.50
Mon, May 30, 2011 (23:45) : London
Wed, June 1, 2011 (05:25) : LONDON ST-PANCRAS €42.50 by TGV Eurostar 9078
Wed, June 1, 2011 (08:50) : PARIS NORD (2h 25m Direct)
Fri, June 3, 2011 (08:24) : PARIS EST €217.40 by TGV Lyria 9211
Fri, June 3, 2011 (22:44) : WIEN WESTBAHNHOF (14h 20m 1 Connection at ZUERICH HB at 13:00)
Sat, June 4, 2011 : Vienna Airport
Vienna = GMT +1
Moscow = GMT +3
Berlin, Amsterdam, Paris = GMT +1
London = GMT+0
Weather Forecast around the world : http://www.weather.com/
Visa Agreement
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 59 TAHUN 2005 TENTANG PENGESAHAN PERJANJIAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK RAKYAT CHINA MENGENAI PEMBEBASAN VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN DINAS
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 6 TAHUN 2008 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH FEDERASI RUSIA TENTANG PEMBEBASAN VISA KUNJUNGAN SINGKAT BAGI PEMEGANG PASPOR DIPLOMATIK DAN DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE RUSSIAN FEDERATION ON VISA EXEMPTION FOR SHORT-TERM VISITS OF THE HOLDERS DIPLOMATIC AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 60 TAHUN 2008 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH FEDERAL AUSTRIA MENGENAI PEMBEBASAN VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE AUSTRIAN FEDERAL GOVERNMENT ON VISA EXEMPTION FOR HOLDERS OF DIPLOMATIC AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 64 TAHUN 2008 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH FEDERASI BRASIL MENGENAI PEMBEBASAN VISA UNTUK PASPOR DIPLOMATIK DAN DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE FEDERATIVE REPUBLIC OF BRAZIL ON VISA EXEMPTION FOR DIPLOMATIC AND OFFICIAL OR SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 18 TAHUN 2009 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK TUNISIA TENTANG PEMBEBASAN VISA BAGI PASPOR DIPLOMATIK DAN DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE REPUBLIC OF TUNISIA ON VISA EXEMPTION FOR DIPLOMATIC AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 37 TAHUN 2009 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK PARAGUAY MENGENAI PEMBEBASAB VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN PASPOR DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIK OF INDONESIA AND THE GOVERNMENT OF THE REPUBLIK OF PARAGUAY ON VISA EXEMPTION FOR DIPLOMATIC, OFFICIAL AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 38 TAHUN 2009 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK AZERBAIJAN MENGENAI PEMBEBASAN VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN PASPOR DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE REPUBLIC OF AZERBAIJAN ON VISA EXEMPTION FOR DIPLOMATIC AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 49 TAHUN 2009 TENTANG PENGESAHAN AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE DEMOCRATIC SOCIALIST REPUBLIC OF SRILANKA ON VISA EXEMPTION FOR HOLDERS OF DIPLOMATIC AND OFFICIAL/SERVICE PASSPORTS (PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK DEMOKRATIK SOSIALIS SRILANKA TENTANG PEMBEBASAN VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN DINAS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 43 TAHUN 2010 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK SLOVAKIA MENGENAI PEMBEBASAN VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN PASPOR DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE SLOVAK REPUBLIC ON VISA EXEMPTION FOR HOLDERS OF DIPLOMATIC PASSPORTS AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 44 TAHUN 2010 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK BULGARIA MENGENAI PEMBEBASAN VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN PASPOR DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE REPUBLIC OF BULGARIA ON VISA EXEMPTION FOR HOLDERS OF DIPLOMATIC AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 13 TAHUN 2011 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH FEDERAL SWISS MENGENAI PEMBEBASAN VISA BERSAMA BAGI PEMEGANG PASSPORT DIPLOMATIK DAN DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE SWISS FEDERAL COUNCIL ON MUTUAL VISA EXEMPTION FOR HOLDERS OF DIPLOMATIC AND SERVICE PASSPORTS)
See other aggreements
Schengen Visa
A Schengen Visa is required by non-EEA nationals wishing to enter the EU for short-term stays not involving employment or self-employed activity.
With offices in the UK, Global Visas is can easily organise Schengen visas through our fully qualified consultants. Our team is qualified to organise all types of visa, including popular choices such as Canada visas or Australia visas.
European Schengen visas, effective from 1995 and named after the Luxembourg village where the original agreement was signed a decade earlier, are designed to facilitate the free and open movement of visitors through Europe.
In practice the Schengen Agreement functions in a similar way to a UK visa, often referred to variously as a UK tourist visa or UK travel visa in that it allows people to enter and leave participating countries for a limited period, after which they must return to their country of residence.
At present, the following countries participate in the scheme. It is worth noting that the United Kingdom and the Republic or Ireland are not currently signatories.
* Austria
* Belgium
* Czech Republic
* Denmark
* Estonia
* Finland
* France
* Germany
* Greece
* Hungary
* Iceland
* Italy
* Latvia
* Lithuania
* Luxembourg
* Malta
* Netherlands
* Norway
* Poland
* Portugal
* Slovakia
* Slovenia
* Spain
* Sweden
* Switzerland
Countries not yet Schengen Area members:
* Bulgaria
* Cyrpus
* Liechtenstein
* Romania
* Serbia
As a specialist immigration consultancy Global Visas can help you to obtain a Schengen visit visa or any other immigration service you may require.
Our immigration consultants can provide immigration lawyer expertise and can manage your visa application at every stage from your initial enquiry through to a comprehensive package of on arrival services.
Address : Schlossberggasse 8, Vienna, Austria A-1130.
Modern Hostel near the famous Schönbrunn Palace and 15 minutes from the centre by underground. FREE breakfast, free bedlinen, free Internet, free WiFi. Dorms with 2, 4, 6 and 7 beds, in total 296 beds! Why look further?! Stay with us!
Shared : €14.50, Private : €15.50. When I chek for May 14 - May 21, 2011, the price is €18 per person.
Modern hostel with 50-year-old tradition!
Welcome to the first hostel in Austria!
Location:
Here you can find the perfect combination of city and green environment, culture and nature, fun and relaxation:
The Youth Hostel Hütteldorf is right on the subway line U4, which brings you in 20 minutes to downtown and in 10 minutes to the Schönbrunn Palace and the Naschmarkt (Vienna’s most popular market). The house itself is situated on the edge of the forest, surrounded by numerous walking and bike trails and a large garden. The unique features and the sensational price make us irresistible to every hostel traveller.
See more : http://www.hostelbookers.com/hostels/austria/vienna/
Cheap Flights from Vienna to Moscow - VIE to MOW
Vienna, AT to Moscow, RU
Depart: Sunday, 5/22/2011 | Return: Tuesday, 5/24/2011
Price US$334 (Roundtrip price), Taxes & fees incl.
Airline : Aeroflot
Depart : VIE at 12:30 AM, Arrive : SVO at 5:05 AM Nonstop, Duration : 2h 35m
Depart : SVO at 4:10 PM, Arrive : VIE 4:50 PM Nonstop, Duration : 2h 40m
Price US$268 (One-way price), Taxes & fees incl.
Airline : Aeroflot
Depart : VIE at 12:30 AM, Arrive : SVO 5:05 AM Nonstop, Duration : 2h 35m
SVO = Shemeretyevo Airport, Moscow
See more : http://www.farecompare.com/flights/Vienna-VIE/Moscow-MOW/market.html
Moscow Hostel ?
Trains between Russia and Germany
There are quite a few ways to travel from Europe to Russia including trains from Germany, Finland, Poland and all of the Baltic States. Please note: a transit visa is required for trains that stop or go through Belarus. If you travel from Germany there are 2 direct trains to Russia one going from Berlin to Moscow and the other from Berlin to St. Petersburg. Also there are a few daily trains from Berlin to Warsaw. To receive Russian train schedules and Russian train ticket prices as well as to have the opportunity to order Russian train tickets online, please use our Russian train tickets page or use the search engine on this page.
Train Berlin №13 Moscow - Berlin (Germany)
Departure Moscow-Belorusskaia : 08:00
Arrival Berlin Zoo (Germany) : 08:52 (next day)
Total hours : 1d 04:52
Price per person for May 23, 2011 : US$ 375 (2nd Class), no 3rd Class.
The route : Moscow Belorusskaia - Viazma - Smolensk - Orsha Center - Minsk Pas - Brest C - Terespol - Lukow - Warszawa Centralna - Warszawa Centralna - Poznan Glowny - Rzepin - Frankfurt Oder - Berlin Ost (East Berlin) - Berlin Gl. - Berlin Zoo.
Train Berlin №14 Berlin (Germany) - Moscow
Departure Berlin (Germany) : 15:24
Arrival Moscow : 20:35
Total hours : 1d 01:11
See more : http://www.expresstorussia.com/moscow-berlin-train.html
Berlin Hostel ?
Trains between Berlin and Amsterdam
Berlin Amsterdam Outbound 25/05/2011 Morning
Outbound : 04:04 at BERLIN HBF
Arrival : 11:08 at AMSTERDAM SCHIPHOL
Duration : 7h 04m (1 connection or transfer)
ICE 646 - Reservation not included
Train 242 - Reservation not included
Flexible Second Class : €114.20
Outbound : 08:04 at BERLIN HBF
Arrival : 15:08 at AMSTERDAM SCHIPHOL
Duration : 7h 04m (Direct)
Train 148 - Reservation not included
Flexible Second Class : €114.20
Outbound : 11:34 at BERLIN HBF
Arrival : 20:25 at AMSTERDAM CS
Duration : 8h 51m (1 connection or transfer)
ICE 599 - Reservation included
ICE 122 - Reservation included
Flexible Second Class : €245.20
Outbound : 14:03 at BERLIN HBF
Arrival : 21:08 at AMSTERDAM SCHIPHOL
Duration : 7h 05m (Direct)
Train 142 - Reservation not included
Flexible Second Class : €114.20
Outbound : 17:45 at BERLIN HBF
Arrival : 09:03 at AMSTERDAM CS
Duration : 15h 18m (1 connection or transfer)
ICE 1093 - Reservation included
Train 418 - Reservation included
Best second class : €188.00
Flexible Second Class : €278.00
See more : http://www.raileurope-world.com/
By bus from Berlin to Amsterdam
Departure : 25-05-2011 (21:30)
Arrival : 26-05-2011 (07:15)
From : Berlin, ZOB Am Funkturm
To : Amsterdam, Amstel Station/Eurolines
Promo (one way) : -
Price (one way) : €58.00
Departure : 26-05-2011 (19:30)
Arrival : 27-05-2011 (05:45)
From : Berlin, ZOB Am Funkturm
To : Amsterdam, Amstel Station/Eurolines
Promo (one way) : €33.00
Price (one way) : €58.00
Departure : 26-05-2011 (21:30)
Arrival : 27-05-2011 (07:15)
From : Berlin, ZOB Am Funkturm
To : Amsterdam, Amstel Station/Eurolines
Promo (one way) : -
Price (one way) : €58.00
Departure : 27-05-2011 (19:30)
Arrival : 28-05-2011 (05:45)
From : Berlin, ZOB Am Funkturm
To : Amsterdam, Amstel Station/Eurolines
Promo (one way) : €40.60
Price (one way) : €58.00
Departure : 27-05-2011 (21:30)
Arrival : 28-05-2011 (07:15)
From : Berlin, ZOB Am Funkturm
To : Amsterdam, Amstel Station/Eurolines
Promo (one way) : -
Price (one way) : €58.00
See more : http://www.touring.de/index.php?id=1089&L=1 or http://www.eurolines.com/
Amsterdam Hostel?
Amsterdam to London by Bus
Departure (Amsterdam) : Sunday, May 29, 2011 8:30 AM
Arrival (London) : Sunday, May 29, 2011 6:15 PM
Departure (Amsterdam) : Sunday, May 29, 2011 10:00 AM
Arrival (London) : Sunday, May 29, 2011 8:10 PM
Departure (Amsterdam) : Sunday, May 29, 2011 7:30 PM
Arrival (London) : Monday, May 30, 2011 6:30 AM
Departure (Amsterdam) : Sunday, May 29, 2011 10:30 PM
Arrival (London) : Monday, May 30, 2011 8:45 AM
Departure (Amsterdam) : Monday, May 30, 2011 8:30 AM
Arrival (London) : Monday, May 30, 2011 6:15 PM
Departure (Amsterdam) : Monday, May 30, 2011 10:00 AM
Arrival (London) : Monday, May 30, 2011 8:10 PM
Departure (Amsterdam) : Monday, May 30, 2011 7:30 PM
Arrival (London) : Tuesday, May 31, 2011 6:30 AM
Departure (Amsterdam) : Monday, May 30, 2011 10:30 PM
Arrival (London) : Tuesday, May 31, 2011 8:45 AM
Departure : Amstelstn.Eurolines Kantoor, Amsterdam
Arrival : Victoria Coach Station, London
Transfer countries : Nederland,Belgie,Frankrijk,Engeland
Cost of your selection One way for 1 Adult (P) : €22.00
S : Standard ticket
P : (Super) Promo ticket
Promo and Super Promo tickets are our best value range of fares available (Promo and Super Promo conditions). If you prefer maximum flexibility to change or cancel your booking we recommend you select a standard ticket.
See more : http://www.eurolines.nl/eng/?lang=ENG
London - Derby (Edensor Village, County Derbyshire) by Bus
Leaving
LONDON (Victoria Coach Station) to Derby — 29 May 2011
*Fares from: Fares based on your passenger selections. The fares listed below are offered only as part of a return journey. Our lowest fares sell out quickly: To avoid disappointment, please choose a fare as soon as possible.
Departs From To Arrives Duration Changes Fares from*
19:30 LONDON (Victoria Coach Station) Derby 22:35 3h 5m 0 £10.50
20:30 LONDON (Victoria Coach Station) Derby 23:50 3h 20m 0 £13.60
23:30 LONDON (Victoria Coach Station) Derby 02:45 3h 15m 0 £5.50
Returning
Derby to LONDON (Victoria Coach Station) — 30 May 2011
*Fares from Fares based on your passenger selections. The fares listed below are offered only as part of a return journey, and may change based on your journey selection. Our lowest fares sell out quickly: To avoid disappointment, please choose a fare as soon as possible.
Departs From To Arrives Duration Changes Fares from*
16:40 Derby LONDON (Victoria Coach Station) 21:30 4h 50m 1 £12.50
17:55 Derby LONDON (Victoria Coach Station) 21:40 3h 45m 0 £5.50
18:45 Derby LONDON (Victoria Coach Station) 23:45 5h 00m 1 £12.50
19:45 Derby LONDON (Victoria Coach Station) 00:10 4h 25m 1 £12.50
See more : http://www.eurolines.co.uk/coach/index.aspx
London - Paris by TGV
See : http://www.raileurope-world.com/
Paris - Vienna by Bus Eurolines
Paris Gallieni Porte Bagnolet to Wien-Erdbergstrasse by Eurolines
departure : Friday 03 June 2011 14:15
arrival : Saturday 04 June 2011 07:15
Price = €50.00
Bus station at Paris : Paris Gallieni Porte Bagnolet, Paris Place de Clichy, Paris Porte de Charenton, Paris Roissy Charles de Gaulle.
See : http://www.eurolines.fr/ENG/?lang=ENG
Misc
Rate :
EUR 1 = IDR 12829.30 (sale) , IDR 12437.30 (buy)
Fri, May 13, 2011 : CKG
Sat, May 14, 2011 : VIENNA
Mon, May 16, 2011 : TM
...
Fri, May 20, 2011 : TM
Sat, May 21, 2011 (00:30 AM) : VIENNA US$268 by Aeroflot
Sat, May 21, 2011 (05:05 AM) : MOSCOW (Shemeretyevo = SVO)
Mon, May 23, 2011 (08:00 AM) : MOSCOW US$ 375 by Train Berlin №13 Moscow - Berlin
Tue, May 24, 2011 (08:52 AM) : BERLIN
Thu, May 26, 2011 (19:30) : Berlin, ZOB Am Funkturm €58.00 by Bus
Fri, May 27, 2011 (05:45) : Amsterdam, Amstel Station/Eurolines
Sun, May 29, 2011 (08:30 AM) : Amsterdam (Amstelstn.Eurolines Kantoor) €22.00 by Bus
Sun, May 29, 2011 (06:15 PM) : London (Victoria Coach Station)
Sun, May 29, 2011 (19:30) : London by Bus £10.50
Sun, May 29, 2011 (22:35) : Derby
Mon, May 30, 2011 (18:45) : Derby by Bus £12.50
Mon, May 30, 2011 (23:45) : London
Wed, June 1, 2011 (05:25) : LONDON ST-PANCRAS €42.50 by TGV Eurostar 9078
Wed, June 1, 2011 (08:50) : PARIS NORD (2h 25m Direct)
Fri, June 3, 2011 (08:24) : PARIS EST €217.40 by TGV Lyria 9211
Fri, June 3, 2011 (22:44) : WIEN WESTBAHNHOF (14h 20m 1 Connection at ZUERICH HB at 13:00)
Sat, June 4, 2011 : Vienna Airport
Vienna = GMT +1
Moscow = GMT +3
Berlin, Amsterdam, Paris = GMT +1
London = GMT+0
Weather Forecast around the world : http://www.weather.com/
Visa Agreement
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 59 TAHUN 2005 TENTANG PENGESAHAN PERJANJIAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK RAKYAT CHINA MENGENAI PEMBEBASAN VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN DINAS
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 6 TAHUN 2008 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH FEDERASI RUSIA TENTANG PEMBEBASAN VISA KUNJUNGAN SINGKAT BAGI PEMEGANG PASPOR DIPLOMATIK DAN DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE RUSSIAN FEDERATION ON VISA EXEMPTION FOR SHORT-TERM VISITS OF THE HOLDERS DIPLOMATIC AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 60 TAHUN 2008 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH FEDERAL AUSTRIA MENGENAI PEMBEBASAN VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE AUSTRIAN FEDERAL GOVERNMENT ON VISA EXEMPTION FOR HOLDERS OF DIPLOMATIC AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 64 TAHUN 2008 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH FEDERASI BRASIL MENGENAI PEMBEBASAN VISA UNTUK PASPOR DIPLOMATIK DAN DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE FEDERATIVE REPUBLIC OF BRAZIL ON VISA EXEMPTION FOR DIPLOMATIC AND OFFICIAL OR SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 18 TAHUN 2009 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK TUNISIA TENTANG PEMBEBASAN VISA BAGI PASPOR DIPLOMATIK DAN DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE REPUBLIC OF TUNISIA ON VISA EXEMPTION FOR DIPLOMATIC AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 37 TAHUN 2009 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK PARAGUAY MENGENAI PEMBEBASAB VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN PASPOR DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIK OF INDONESIA AND THE GOVERNMENT OF THE REPUBLIK OF PARAGUAY ON VISA EXEMPTION FOR DIPLOMATIC, OFFICIAL AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 38 TAHUN 2009 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK AZERBAIJAN MENGENAI PEMBEBASAN VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN PASPOR DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE REPUBLIC OF AZERBAIJAN ON VISA EXEMPTION FOR DIPLOMATIC AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 49 TAHUN 2009 TENTANG PENGESAHAN AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE DEMOCRATIC SOCIALIST REPUBLIC OF SRILANKA ON VISA EXEMPTION FOR HOLDERS OF DIPLOMATIC AND OFFICIAL/SERVICE PASSPORTS (PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK DEMOKRATIK SOSIALIS SRILANKA TENTANG PEMBEBASAN VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN DINAS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 43 TAHUN 2010 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK SLOVAKIA MENGENAI PEMBEBASAN VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN PASPOR DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE SLOVAK REPUBLIC ON VISA EXEMPTION FOR HOLDERS OF DIPLOMATIC PASSPORTS AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 44 TAHUN 2010 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH REPUBLIK BULGARIA MENGENAI PEMBEBASAN VISA BAGI PEMEGANG PASPOR DIPLOMATIK DAN PASPOR DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE GOVERNMENT OF THE REPUBLIC OF BULGARIA ON VISA EXEMPTION FOR HOLDERS OF DIPLOMATIC AND SERVICE PASSPORTS)
PERATURAN PRESIDEN REPUBLIK INDONESIA NOMOR 13 TAHUN 2011 TENTANG PENGESAHAN PERSETUJUAN ANTARA PEMERINTAH REPUBLIK INDONESIA DAN PEMERINTAH FEDERAL SWISS MENGENAI PEMBEBASAN VISA BERSAMA BAGI PEMEGANG PASSPORT DIPLOMATIK DAN DINAS (AGREEMENT BETWEEN THE GOVERNMENT OF THE REPUBLIC OF INDONESIA AND THE SWISS FEDERAL COUNCIL ON MUTUAL VISA EXEMPTION FOR HOLDERS OF DIPLOMATIC AND SERVICE PASSPORTS)
See other aggreements
Schengen Visa
A Schengen Visa is required by non-EEA nationals wishing to enter the EU for short-term stays not involving employment or self-employed activity.
With offices in the UK, Global Visas is can easily organise Schengen visas through our fully qualified consultants. Our team is qualified to organise all types of visa, including popular choices such as Canada visas or Australia visas.
European Schengen visas, effective from 1995 and named after the Luxembourg village where the original agreement was signed a decade earlier, are designed to facilitate the free and open movement of visitors through Europe.
In practice the Schengen Agreement functions in a similar way to a UK visa, often referred to variously as a UK tourist visa or UK travel visa in that it allows people to enter and leave participating countries for a limited period, after which they must return to their country of residence.
At present, the following countries participate in the scheme. It is worth noting that the United Kingdom and the Republic or Ireland are not currently signatories.
* Austria
* Belgium
* Czech Republic
* Denmark
* Estonia
* Finland
* France
* Germany
* Greece
* Hungary
* Iceland
* Italy
* Latvia
* Lithuania
* Luxembourg
* Malta
* Netherlands
* Norway
* Poland
* Portugal
* Slovakia
* Slovenia
* Spain
* Sweden
* Switzerland
Countries not yet Schengen Area members:
* Bulgaria
* Cyrpus
* Liechtenstein
* Romania
* Serbia
As a specialist immigration consultancy Global Visas can help you to obtain a Schengen visit visa or any other immigration service you may require.
Our immigration consultants can provide immigration lawyer expertise and can manage your visa application at every stage from your initial enquiry through to a comprehensive package of on arrival services.
Subscribe to:
Posts (Atom)







